Client Side View
Core Impact 's Client Side view allows you to customize and manage the client-side target information generated by your client-side penetration tests. Client-side entities take the form of Email addresses that may or may not contain an associated user's name.
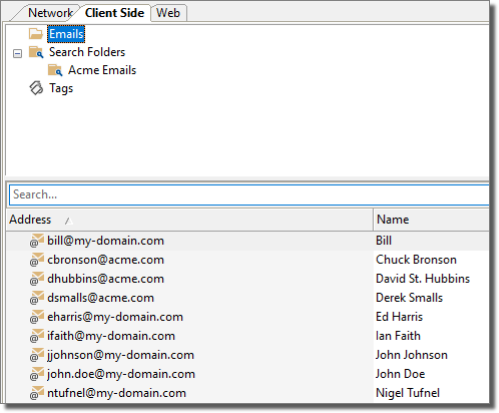
figure 31 - Entity View - Client Side View
Core Impact's client-side entities allow you to manipulate and view target information for client-side exploits and modules, and execute attacks against targets in a convenient and customized manner. Entities are added to this view from the Client Side Information Gathering RPT, client-side modules such as HTTP Email Address Grabber, or by adding them manually.
To manually add an entity to the Client-side view:
- Activate the Client Side tab of the Entity View.
- Right-click on the Emails folder.
- Select New, then select Email...
-
Enter the email Address and Name of the user.
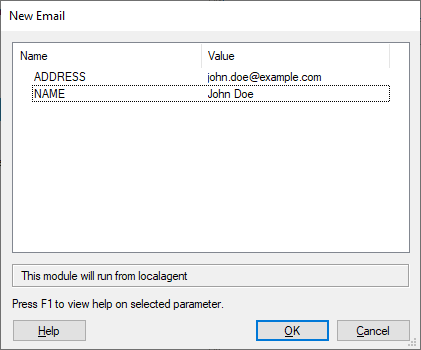
Click the OK button.
The New Email module will run and, after a brief moment, you will see the new email appear in the Entity View.
Entity Tags and Search Folders further enhance the usability of this view.
When you click on an email entity, its Quick Information will show the entity's details including where the email address was discovered (under Sources). This can be useful if the Client Side Information Gathering step found email addresses from the Internet - if you know where they were found, you can take steps to have them removed.
You can launch attacks against specific client-side entities in the Client-side View by using the Client-side RPT wizards or manually dragging modules from Core Impact Modules View and dropping them onto a specific search folder or entity. For example, if you wanted to launch an email exploit (such as "Firefox compareTo exploit") against a group of targets, dragging and dropping the exploit onto a search folder would result in the exploit running against all email addresses in that folder. Alternatively, for a more focused attack, you could drag the exploit onto a single person in the same folder, which would result in the exploit attacking only that entity. The above scenario can more easily be performed using the Client-side RPT Attack and Penetration wizard.
For information on using Core Impact modules, see Working With Modules.