Client Side Attack Phase: Attack and Penetration
Once the target email addresses have been identified and added to Core Impact's database, you can then use the Client-side Attack and Penetration step of the Client-side RPT process to attack one or more end-users. This wizard guides you step-by-step through the process of selecting email address targets, the attack type, selecting the attack category (e.g., web browser, email client, attachment, or Trojan attack), and selecting an email template to use for the client-side attack. You can customize each email to increase the authenticity of the attack and the likelihood that an untrained end-user will fall for a social engineering attack. If an end-user's system is compromised with a client-side attack, an agent is deployed and you can then pivot (see Set as Source) from that agent to run network attacks using the Network RPT process from inside your network thus bypassing any perimeter defenses.
You can also opt to deliver a client-side exploit using a means other than email. For example, you may want to load the attack files onto a USB drive or otherwise distribute the files to target users. For details on this process see the Decoupling the Attack Vector from the Exploit Mechanism section.
The Client-side Attack and Penetration wizard has many option paths that can vary depending on the settings you choose. To begin the Attack and Penetration:
- Ensure that the Client-side RPT is activated.
- Click Client-side Attack and Penetration to open the wizard and press Next to start.
-
Select the Attack Type
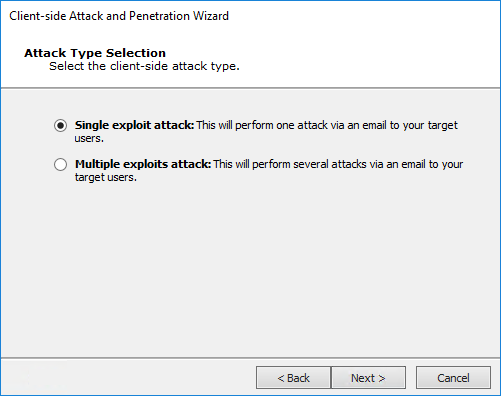
Single exploit attack - This option will send 1 attack in an email to your targets.
Multiple exploits attack - This option will send several different attacks via email to your targets.
Below please find the configuration settings for each of the available options:
-
Targeting with Single Exploit.
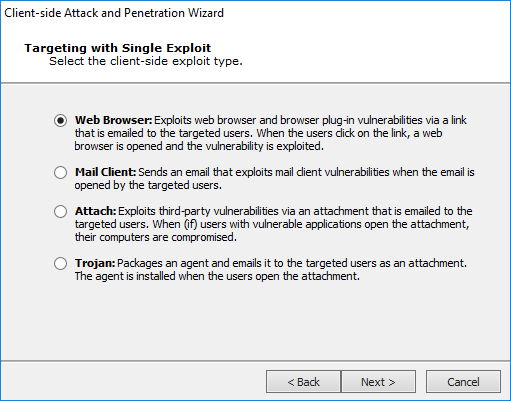
Select the desired Exploit type and press Next to continue.
Web Browser - These attacks take advantage of web browser vulnerabilities or web browser plug-ins. The email recipient must click on a link that opens a web page. The web page will be pre-established by Core Impact to launch an attack against the user's system.
Mail Client - These exploits take advantage of vulnerabilities in the recipient's email client software.
Attach - These attacks require that an attachment be opened by the email recipient. The attachment will be pre-designed to exploit vulnerabilities in a third party application.
Trojan - These involve attaching an agent to the email. If a user executes the attachment, the agent is deployed on their machine. This option includes some unique configurations - see Settings for Trojan Attack.
-
Exploit selection method
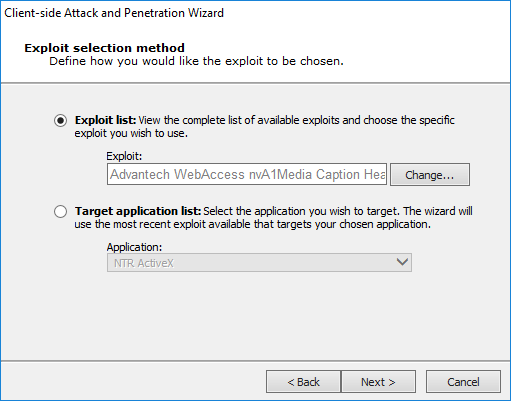
Exploit List - Select this option if you want to specify which exploit should be targeted on compromised hosts. Then click the Change ... button to select an exploit or module name to send in your attack.
Target Application List - Select this option if you want to specify an application to target, then select from the Application drop-down menu. Core Impact will send the most recent exploit for that application.
-
Email Target Selection
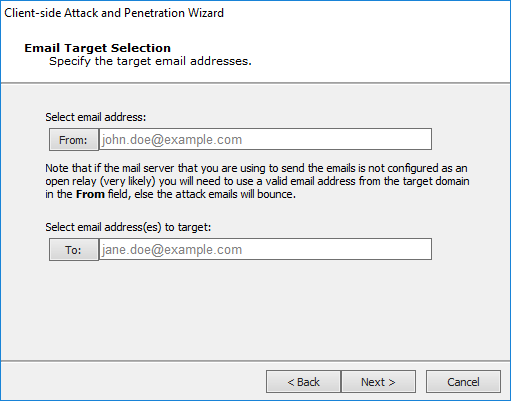
Click the From: button to select an address that will appear in the header of the email being sent. Click the To: button to select recipient email addresses from the Entity Database's Client Side View.
If the desired addresses are not yet in the Client Side View, you can add them using the same procedure as if you were working in the Client Side View directly. Right-click in the view, then select New..., then select Email.
-
Email Template Selection
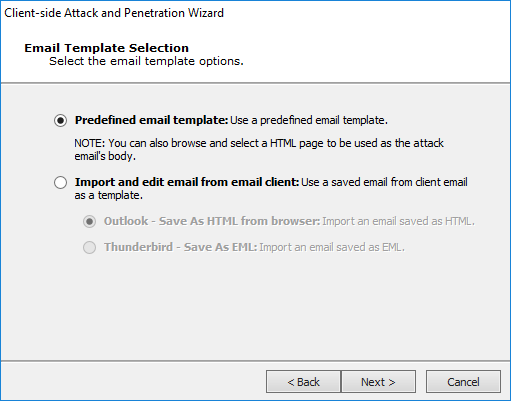
Predefined email template - Core Impact includes several email templates that you can use to craft your Client-side attack.
Import and edit email from email client - You can use an actual email (from either Outlook or Thunderbird) as the basis for a new template.
-
End User Experience
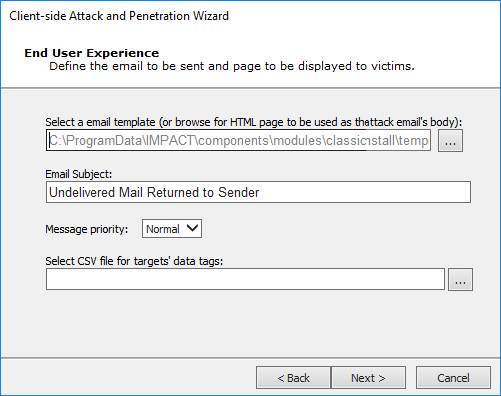
Core Impact ships with several email templates that are located in:
%ProgramData%\IMPACT\components\modules\classic\install\templatesYou can customize these templates to maximize the chance that your users will take action in the email. Click the ellipsis button to select a new template, or to modify the one that is selected. When working on the Email template, click to the Edit tab and modify as needed. In addition to customizing the body text, you can add tags to the email so that it contains data that is specific to the recipient and will therefor appear more legitimate.
Email Subject: Enter the text you would like to appear as the subject of the email. This will be populated by default but you can over-write the text.
Select CSV file for targets' data tags: By default, the email templates only include a handful of basic tags. If you'd like to add more tags to the email, you can import the tags and their values using a .csv file. The .csv file must be formatted in the following way:
- Row 1: the names of the tag fields. The first tag name must be 'target'
- Rows 2 - x: the values of the tags. The 'target' value must be the email address of the target
Below is an example of how the .csv may appear:
target, nickname, company, position john.doe@example.com, Johnny, JD Corp, VP of Customer Support az@core.sec, Azzo, JD Corp, Secretary After importing the .csv file, you can edit the template and reference content from the .csv file by using the custom tag:
<%csv:[field_name]%>. For example,<%csv:nickname%>or<%csv:position%>. -
Client-side Attack Setup
Select additional options to configure.
-
Advanced Options
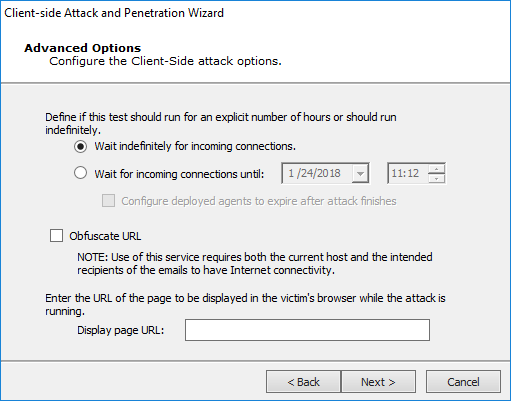
Wait indefinitely for incoming connections: Core Impact will wait indefinitely for connections from email recipients.
Wait for incoming connections until: You can specify the date and time when Core Impact will stop accepting incoming connections from email recipients and, optionally, whether the deployed agents should expire following the completion of the attack.
Obfuscate URL: Optionally select a URL obfuscation service to mask the URL that will be used in the email.
Enter a Display Page URL which represents the web page the attack target user will see while the attack is in progress.
Press Next or Finish to continue.
-
Agent Communication Settings
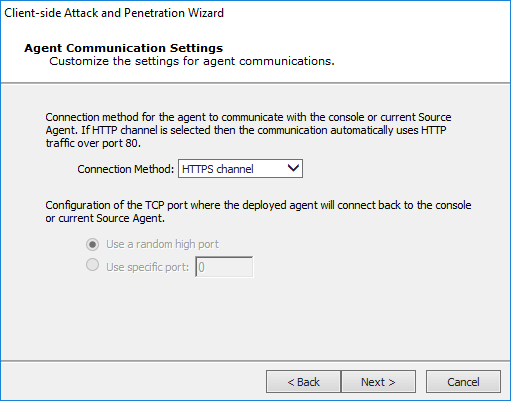
Select a Connection Method as one of the following:
- Connect from target
- HTTP Channel
- HTTPS Channel
Optionally, enter an Incoming connection port for agents to connect to on the Core Impact console or the current Source Agent.
Press Next or Finish to continue.
-
Post Exploitation Options
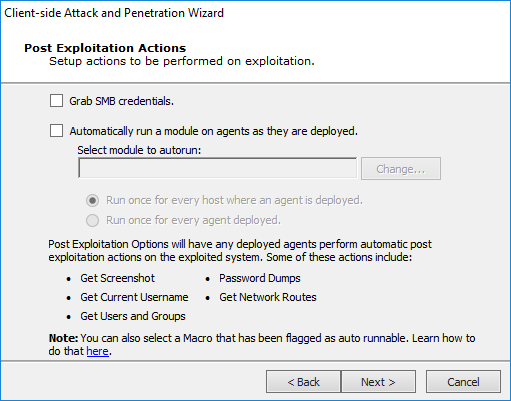
Grab SMB credentials: With this option checked, Core Impact will attempt to force the target to authenticate to the web server with its encrypted SMB credentials (NTLM challenge/response). If successful, Core Impact operators can export these challenge/responses in John the Ripper format. Check the SMB Encrypted Credentials Exporter module for more information.
Automatically run modules on agents as they are deployed: With this option checked, Core Impact will automatically run a module that you select when an agent is deployed on a target system. You can then determine whether the module is executed once per exploited host or once per deployed agent. In the below example, the Make Agent Persistent module will be run for each host where an agent is deployed.
Press Next or Finish to continue.
-
Email Sending Settings
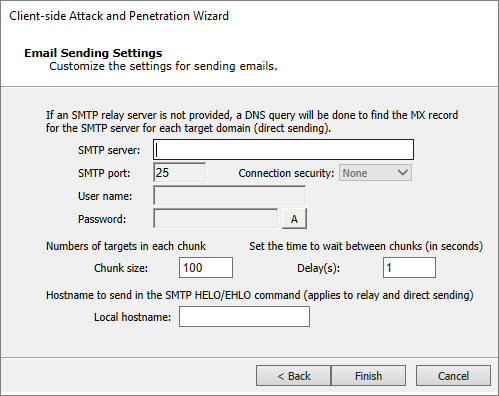
Enter the SMTP Server and SMTP Port for your email SMTP server. Optionally, choose STARTTLS as the Connection security and then enter the Username and Password for your SMTP server.
If you want to limit the number of emails that are sent at one moment, set a Chunk Size. This value will determine the maximum number of emails that will be sent at one time.
Enter the Delay (in seconds) that you want Core Impact to wait in between sending chunks of email in this attack.
Set a Local Hostname if the fully qualified domain name (FQDN) of the machine where Core Impact is running doesn't work with the SMTP server (for example, messages are ignored).
Press Next or Finish to continue.
-
Web Server Settings
The web server used in the attack can be run on any active agent that was previously deployed. This feature is convenient in situations where the potential targets might not be able to connect directly to the machine where Core Impact is running. When using the localagent (the default) for the web server, make sure the target workstations will be able to connect to it. If the computer running Core Impact is sitting behind a NAT device, you must activate and configure the NAT support in Network Options and configure your NAT device to redirect the appropriate ports back to the computer running Core Impact. Check to ensure that the Port value of the Web Server module (80 by default) is also redirected.
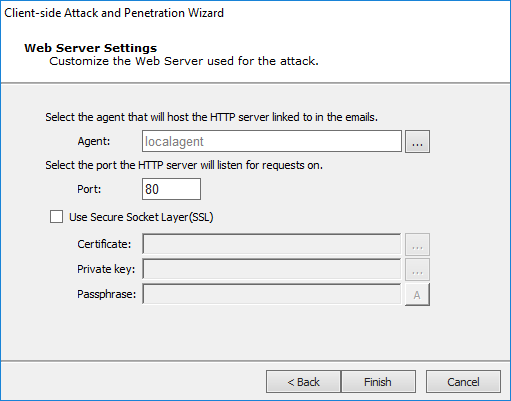
Enter the Agent and URL components to be sent to attack target users:
Agent: Select the agent that will host the HTTP server linked to in the emails.
Port: Enter the port on which the HTTP server will listen.
Check the Use Secure Socket Layer option and configure, if using.
Press Next or Finish to continue.
-
-
Email Target Selection

Click the From: button to select an address that will appear in the header of the email being sent. Click the To: button to select recipient email addresses from the Entity Database's Client Side View.
If the desired addresses are not yet in the Client Side View, you can add them using the same procedure as if you were working in the Client Side View directly. Right-click in the view, then select New..., then select Email.
-
Email Template Selection

Predefined email template - Core Impact includes several email templates that you can use to craft your Client-side attack.
Import and edit email from email client - You can use an actual email (from either Outlook or Thunderbird) as the basis for a new template.
-
End User Experience

Core Impact ships with several email templates that are located in:
%ProgramData%\IMPACT\components\modules\classic\install\templatesYou can customize these templates to maximize the chance that your users will take action in the email. Click the ellipsis button to select a new template, or to modify the one that is selected. When working on the Email template, click to the Edit tab and modify as needed. In addition to customizing the body text, you can add tags to the email so that it contains data that is specific to the recipient and will therefor appear more legitimate.
Email Subject: Enter the text you would like to appear as the subject of the email. This will be populated by default but you can over-write the text.
Select CSV file for targets' data tags: By default, the email templates only include a handful of basic tags. If you'd like to add more tags to the email, you can import the tags and their values using a .csv file. The .csv file must be formatted in the following way:
- Row 1: the names of the tag fields. The first tag name must be 'target'
- Rows 2 - x: the values of the tags. The 'target' value must be the email address of the target
Below is an example of how the .csv may appear:
target, nickname, company, position john.doe@example.com, Johnny, JD Corp, VP of Customer Support az@core.sec, Azzo, JD Corp, Secretary After importing the .csv file, you can edit the template and reference content from the .csv file by using the custom tag:
<%csv:[field_name]%>. For example,<%csv:nickname%>or<%csv:position%>. -
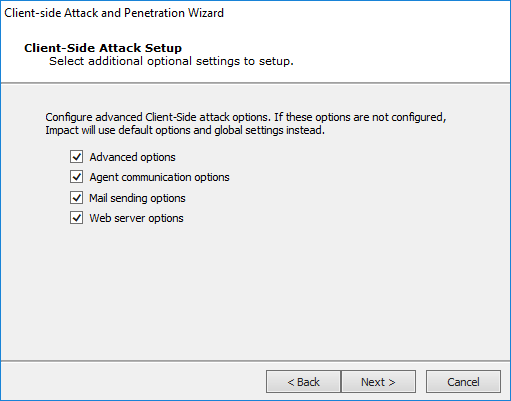
Client-side Attack Setup
Select additional options to configure.
-
Advanced Options

Wait indefinitely for incoming connections: Core Impact will wait indefinitely for connections from email recipients.
Wait for incoming connections until: You can specify the date and time when Core Impact will stop accepting incoming connections from email recipients and, optionally, whether the deployed agents should expire following the completion of the attack.
Obfuscate URL: Optionally select a URL obfuscation service to mask the URL that will be used in the email.
Enter a Display Page URL which represents the web page the attack target user will see while the attack is in progress.
Press Next or Finish to continue.
-
Agent Communication Settings

Select a Connection Method as one of the following:
- Connect from target
- HTTP Channel
- HTTPS Channel
Optionally, enter an Incoming connection port for agents to connect to on the Core Impact console or the current Source Agent.
Press Next or Finish to continue.
-
Email Sending Settings

Enter the SMTP Server and SMTP Port for your email SMTP server. Optionally, choose STARTTLS as the Connection security and then enter the Username and Password for your SMTP server.
If you want to limit the number of emails that are sent at one moment, set a Chunk Size. This value will determine the maximum number of emails that will be sent at one time.
Enter the Delay (in seconds) that you want Core Impact to wait in between sending chunks of email in this attack.
Set a Local Hostname if the fully qualified domain name (FQDN) of the machine where Core Impact is running doesn't work with the SMTP server (for example, messages are ignored).
Press Next or Finish to continue.
-
Web Server Settings
The web server used in the attack can be run on any active agent that was previously deployed. This feature is convenient in situations where the potential targets might not be able to connect directly to the machine where Core Impact is running. When using the localagent (the default) for the web server, make sure the target workstations will be able to connect to it. If the computer running Core Impact is sitting behind a NAT device, you must activate and configure the NAT support in Network Options and configure your NAT device to redirect the appropriate ports back to the computer running Core Impact. Check to ensure that the Port value of the Web Server module (80 by default) is also redirected.

Enter the Agent and URL components to be sent to attack target users:
Agent: Select the agent that will host the HTTP server linked to in the emails.
Port: Enter the port on which the HTTP server will listen.
Check the Use Secure Socket Layer option and configure, if using.
Press Next or Finish to continue.
-
When you have reached the end of your configurations, click the Finish button. The Wizard will close and the Client-side Attack and Penetration modules will begin. You will be able to see progress in the Executed Modules pane. Once completed, the Module Output pane will display the step's findings.
Settings for Trojan Attack
-
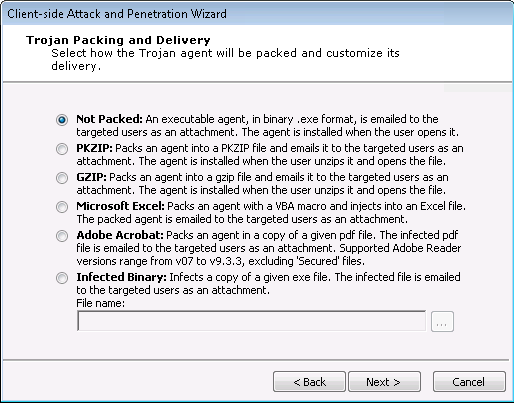
Select the Trojan Packing and Delivery:
This step allows you to determine how the Trojan attack is packaged before it is emailed to your targets. Select from the following options:
- Not Packed: Trojan will be sent as an executable file (.exe).
- PKZIP: Trojan will be sent as a PKZIP compressed file.
- GZIP: Trojan will be sent as a GZIP compressed file.
- Microsoft Excel: This option will package the trojan inside of a Microsoft Excel macro. Browse to select your Excel file and then click the Next button to configure the Duration of Client-side Attack.
- Adobe Acrobat: This option will package an agent into a .pdf file. Browse to select your .pdf file and then click the Next button to configure the Duration of Client-side Attack.
- Infected binary:This option will package an agent into an .exe file. Browse to select your .exe file and then click the Next button to configure the Duration of Client-side Attack.
Then click the Next button.
Trojan Packing and Delivery
-
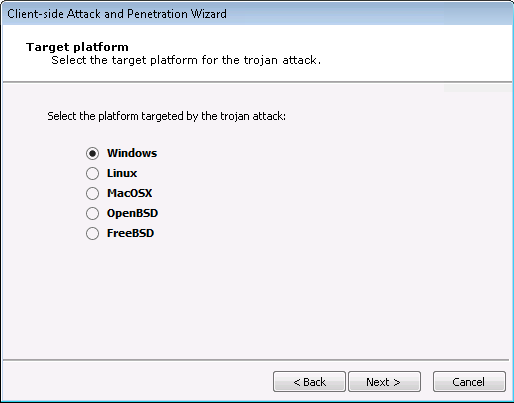
Select the Target Platform:
For Trojan attacks, select the platform of the system where the Trojan is going to be received and launched.
Then click the Next button and skip to the Duration of Client-side Attack section of this guide.
Target Platform
Advanced Client-Side Attack Options
Decoupling the Attack Vector from the Exploit Mechanism
Client-side testing in Core Impact allow you to send email to target users and have their actions in the email trigger an exploit. You may, however, wish to deliver the attack with a means other than email (e.g. a file share server or site or via a USB stick). If so, you can accomplish this by launching the exploit module manually and changing the delivery method. To do this:
- Click the Modules tab to access the Modules View (make sure the Client Side tab in the Entity view is active).
- Expand the Exploits folder, then the Client Side folder.
- Under the Client Side folder, double-click the exploit that you wish to launch. This opens the exploit's email template.
-
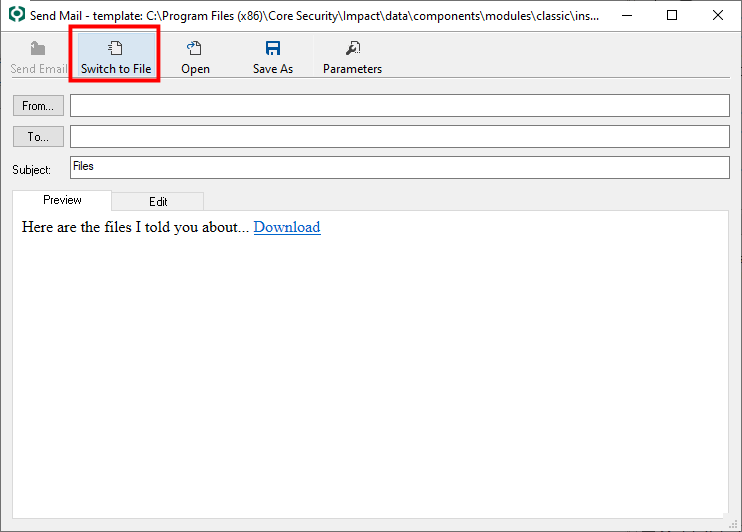
On the template window, click the Switch to File button.
-
The form will change to the File Generation for Decoupled Attack form. Fill in the two fields.
Attack Description: A text description of the attack file.
Select location to save ... : The path to the folder on your system where you want Core Impact to save the attack file. Use the ellipsis (
 ) button to navigate to the desired location.
) button to navigate to the desired location.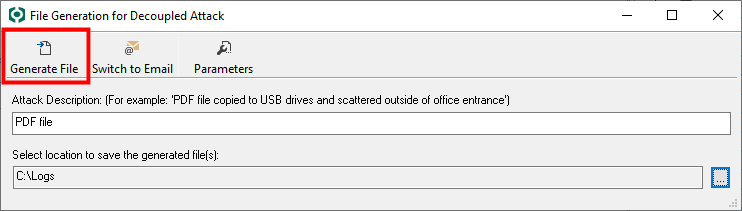
-
Press the Generate File button.
Core Impact generates the attack file(s) and places it in the location you specified. You can then deliver the attack according to your test plan.
Agent Auto Injection
Client-side exploits automatically enable the deployed agent to escape to a different process rather than running in the one originally exploited. This is an important discriminator of Core Impact commercial-grade exploits because it ensures that the agent will continue working even after the end-user exits the client-side application or if the client-side application becomes unstable after exploitation.
For example, the IE IFRAME Buffer Overflow exploit takes advantage of a vulnerability in IE and deploys an agent into IE's iexplore.exe process. After exploitation, IE may become unresponsive, and it is very likely that the end-user driving it will restart it, eliminating the agent in the process. In this example, after the agent is successfully deployed the Module Log says:
escaping to process: c:\winnt\explorer.exe, pid: 1408
This log line indicates that the agent will attempt to escape to the explorer.exe process on PID 1408. After injecting a new agent into this process, the new agent will connect back to the console and the old agent will terminate. That is why you will see two new agents appear on the Entity View (one alive and one uninstalled) when using exploits with this functionality. To learn more about agent auto injection see Agent Auto Injection.
Agent Connection Parameters
By default, when a Client-side exploit is executed, the new agent communicates back to the source agent (usually the localagent). If you want to use a different agent for this, you can do so by configuring and launching the exploit manually through the Modules View.
To do this:
- Click the Modules tab to access the Modules View.
- Expand the Exploits folder, then the Client Side folder.
- Under the Client Side folder, double-click the exploit that you wish to launch. This opens the exploit's email template.
-
On the template window, click the Parameters button.
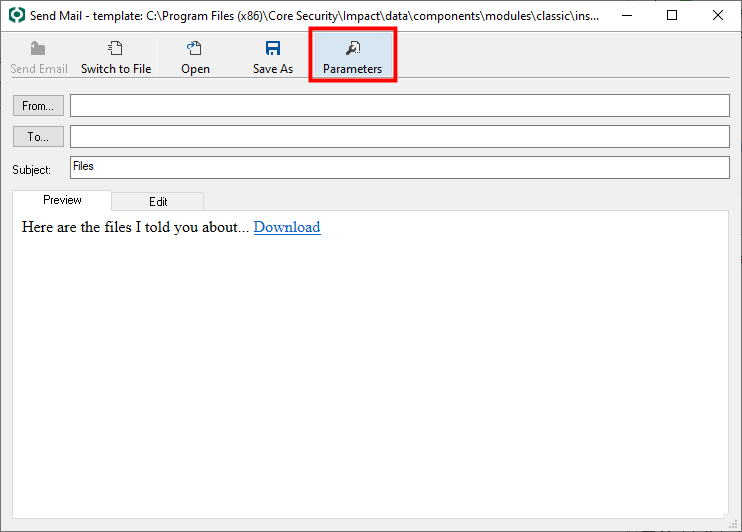
The exploit's parameters form opens.
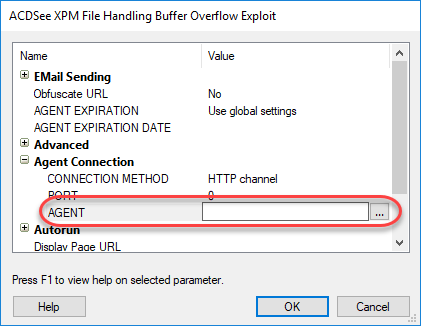
-
Expand the Agent Connection section.
To select a different agent for the exploit's agent to communicate back to, click in the Agent field and then click the ellipsis (
 ) button.
) button. - In the Select Agent Connection window, locate and place a check next to the desired agent, then click the OK button.
- Continue to configure the client-side exploit and launch the attack.