![]()
HTTPS is required both for IIS -> EFT communications and to enable recipients to pick up their files.
The Secure Ad Hoc Transfer (SAT) Module is installed on the IIS server computer. The IIS server computer can be on the same server computer where EFT Server is running, or on a separate computer. To minimize system resources, it is recommended that EFT Server and IIS be installed on the same server computer; however, if system resources are not a factor, then placing EFT Server and IIS on separate server computers may facilitate installation and setup.
Common Deployment Methods
Place IIS with SAT inside your network. Access to the SAT Web interface is limited to internal users who can exchange files with external users. This method can be used with or without DMZ Gateway.
Place IIS with SAT in the DMZ. Access to the SAT Web interface is available to external users who can exchange files with internal users or other external users. GlobalSCAPE recommends against placing the IIS server with SAT in the DMZ to prevent possible misuse of the SAT module.
If you plan to have EFT Server and IIS on the same system, you must have:
HTTPS enabled on EFT Server at the Site level.
Your EFT Administrator username and password
EFT Server and IIS both running before the Secure Ad Hoc Transfer module is installed.
If you plan on having EFT Server and IIS on different systems, you must have:
HTTPS enabled on EFT Server at the Site level
Your EFT Administrator username and password
The remote administrator enabled in EFT Server.
EFT Server's IP address accessible from EFT Server running IIS
EFT Server and IIS both running before the Secure Ad Hoc Transfer module is installed
|
|
HTTPS is required both for IIS -> EFT communications and to enable recipients to pick up their files. |
One common deployment scheme is to place both IIS and EFT Server inside your network. Only internal users are able to access the Secure Ad Hoc Transfer Web interface and exchange files with users outside the network.
The architectural diagram below demonstrates this setup with EFT Server and IIS both on separate boxes. It also assumes the use of the DMZ Gateway; without it, you would need to configure the solution differently, so that recipients can reach EFT Server.
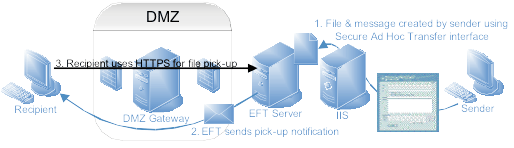
The sender, inside your network, connects to the Web form provided by IIS running the Secure Ad Hoc Transfer module page.
Secure Ad Hoc Transfer on IIS then offloads the file to EFT Server, creates a notification message, and sends that directly to the recipient through your SMTP server.
The recipient connects using the link-back https hyperlink to EFT Server to download the available files and, if applicable, uploads files back to EFT Server for later pick-up by the originator (sender).
You can deploy Secure Ad Hoc Transfer in the DMZ so that clients or partners can initiate a send either to one of your users, or to a third party. GlobalSCAPE recommends against this approach to avoid potential misuse of the Secure Ad Hoc Transfer module.
Secure Ad Hoc Transfer System Requirements