The PCI DSS Compliance Report displays the requirement name, status (PASSED, FAILED, WARNING), description of the requirement, notes that you typed in the Warning box (explanation, justification, or compensating control), report name, and date the report was generated, and description of the report. The report is grouped by and sorted by PCI DSS Requirement.

If the report is generated after the HSM trial has expired, the report contains the following statement instead of the standard report:
The HSM has expired. Please contact your GlobalSCAPE sales representative or visit http://www.globalscape.com/eft for more details.
The status of the PCI DSS requirements described below appears in the report:
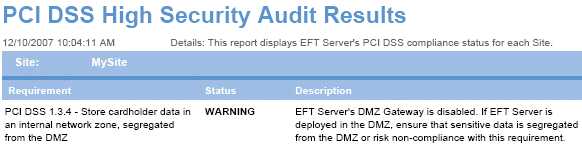
EFT Server determines whether the DMZ Gateway is enabled, and whether a socket connection to the DMZ Gateway can be made. Possible outcomes include:
|
Requirement |
Status |
Description |
|
PCI DSS 1.3.7 Perimeter Security |
PASSED |
EFT Server's DMZ Gateway enabled and connected |
|
PCI DSS 1.3.7 Perimeter Security |
WARNING |
EFT Server's DMZ Gateway IP and port defined; however EFT Server cannot connect to the DMZ Gateway |
|
PCI DSS 1.3.7 Perimeter Security |
WARNING |
EFT Server's DMZ Gateway is disabled. If EFT Server is deployed in the DMZ, ensure that sensitive data is segregated from the DMZ or risk non-compliance with this requirement. |
EFT Server determines whether any default values are specified for Admin login port (1100), DMZ Gateway Server port (44500), FTP banner message, or SFTP banner message. Possible report outcomes include:
|
Requirement |
Status |
Description |
|
PCI DSS 2.1 Change Vendor Defaults |
PASSED |
No EFT Server supplied default values are being used (ports and banner messages checked) |
|
PCI DSS 2.1 Change Vendor Defaults |
FAILED |
[Admin Login Port, DMZ Gateway Connection Port, Default FTP Banner Message, or Default SFTP Banner Message] is the same as the default supplied. You should change the default port to a value between 1024 and 65535. |
|
|
A separate failure description appears in the report for each setting that uses a default value. |
EFT Server determines whether any non-secure protocols are enabled for the Site, Settings Template, or user account and reports for each Site, Settings Template, or user account failed. Possible report outcomes include:
|
Requirement |
Status |
Description |
|
PCI DSS 2.2.2 Disable all non-secure protocols |
PASSED |
Only secure protocols are being used for this Site. |
|
PCI DSS 2.2.2 Disable all non-secure protocols |
FAILED |
[FTP or HTTP] protocol is enabled for [Site, Settings Template, or specific user name]. You should disable these protocols. Alternately, you must have ample justification and documentation per PCI 1.1.6 and 1.1.7 for continued use of non-secure protocols. |
EFT Server determines whether disk quota is enabled, auto-ban meter is set to Off, Very Low, or Low, or the option to pass login credentials to Event Rules is enabled, and whether site-to-site transfers are enabled. Possible report outcomes include:
|
Requirement |
Status |
Description |
|
PCI DSS 2.2.3 Configure security system parameters set to prevent misuse |
PASSED |
System security parameters are configured to prevent misuse. |
|
PCI DSS 2.2.3 Configure security system parameters set to prevent misuse |
WARNING |
The option to pass user login credentials as an event rule variable (Site settings) should be disabled to comply with PCI 2.2.3 |
|
PCI DSS 2.2.3 Configure security system parameters set to prevent misuse |
WARNING |
Auto-ban connection flood sensitivity is too low. Please set to Medium, High, or Very High to better comply with this requirement. |
|
PCI DSS 2.2.3 Configure security system parameters set to prevent misuse |
WARNING |
You have not specified a disk quota for a user or Settings Template. A malicious user could upload more data than available disk space, effectively disabling EFT Server. |
|
PCI DSS 2.2.3 Configure security system parameters set to prevent misuse |
WARNING |
Anti-timeout blocking is currently disabled for [Site]. |
|
PCI DSS 2.2.3 Configure security system parameters set to prevent misuse |
WARNING |
Site-to-site transfers are currently allowed for [Site]. |
|
PCI DSS 2.2.3 Configure security system parameters set to prevent misuse |
WARNING |
NOOP FTP command is currently allowed for [Site]. |
EFT Server determines whether remote administration is enabled, and if so, if SSL is enabled. Possible report outcomes include:
|
Requirement |
Status |
Description |
|
PCI DSS 2.3 Encrypt all non-console access |
PASSED |
Non-console administrative access is securely configured. |
|
PCI DSS 2.3 Encrypt all non-console access |
FAILED |
Remote administration is enabled without SSL turned on. Either enable SSL or disable remote access. |
|
PCI DSS 2.3 Verify strong encryption is invoked before password is requested |
PASSED |
The option to send users their login credentials over e-mail is enabled for this Site. You should consider disabling this option. |
|
PCI DSS 2.3 Verify strong encryption is invoked before password is requested |
FAILED |
EFT Server does not e-mail users their passwords |
EFT Server determines whether any Clean-up Actions are defined, and warns if none is found. Possible report outcomes include:
|
Requirement |
Status |
Description |
|
PCI DSS 3.1 Develop a data retention and disposal policy |
PASSED |
Does not appear in report if passed. |
|
PCI DSS 3.1 Develop a data retention and disposal policy |
WARNING |
No disk quota is set for [Site]. Enable disk quotas to limit data storage amounts to what is required for business purposes according to your company's data retention policy. |
|
PCI DSS 3.1 Develop a data retention and disposal policy |
WARNING |
No Clean-up Action was found. Define a Clean-up Action in a Scheduler (Timer) Event Rule to automate the disposal of deprecated data. |
EFT Server determines whether the EFS option is enabled on the VFS root folder and physical virtual subfolders only (not on the files within those folders) and warns if EFS is enabled. Possible report outcomes include:
|
Requirement |
Status |
Description |
|
PCI DSS 3.4.1 Logical access and decryption keys disk must be managed independently for disk-level encryption |
PASSED |
Encrypting File System (EFS) is not enabled through the administration interface. |
|
PCI DSS 3.4.1 Logical access and decryption keys disk must be managed independently for disk-level encryption |
WARNING |
Encrypted File Store (EFS) is enabled in the Virtual File System. Make sure you are using an alternate disk or file encryption method as EFS encryption does not comply with PCI 3.4.1 |
EFT Server determines whether the primary SSL or SFTP key is using a 512-bits-or-fewer key length. Possible report outcomes include:
|
Requirement |
Status |
Description |
|
PCI DSS 3.6.1 Generation of strong keys |
PASSED |
Strong server SSL/SFTP keys used. |
|
PCI DSS 3.6.1 Generation of strong keys |
WARNING |
Site [SSL|SFTP] certificate key has a length of 1024 bits. While 1024 bits is acceptable, 2048 or higher bit-length keys are recommended. |
|
PCI DSS 3.6.1 Generation of strong keys |
FAILED |
Server administration [SSL|SFTP] certificate key has a length of [n] bits. While 1024 bits is acceptable, 2048 or higher bit-length keys are recommended. |
EFT Server determines whether certificate keys used on EFT Server are current. The HSM checks the key length and expiration date only for EFT Server's SSL certificates (i.e. administration certificate and site certificates); client certificates (i.e. trusted certificates) are not checked. Possible report outcomes include:
|
Requirement |
Status |
Description |
|
PCI DSS 3.6.5 Key management, destruction, or revocation of old keys |
PASSED |
All certificates are current. |
|
PCI DSS 3.6.5 Key management, destruction, or revocation of old keys |
WARNING |
One or more SSL certificates or SFTP keys have expired. You should remove that key from the key manager and replace it with a current version. |
EFT Server determines whether any weak ciphers (<128 bit) or any version other than TLS or SSLv3 are enabled. Possible report outcomes include:
|
Requirement |
Status |
Description |
|
PCI DSS 4.1 Use strong cryptographic ciphers for transport protocols |
PASSED |
Strong ciphers and protocols are being used. |
|
PCI DSS 4.1 Use strong cryptographic ciphers for transport protocols |
FAILED |
SSL cipher string was manually defined or unable to ascertain which ciphers were chosen. Please select SSL ciphers from the provided list (Security page in Server tab). |
|
PCI DSS 4.1 Use strong cryptographic ciphers for transport protocols |
FAILED |
One or more ciphers are less than 128 bit. Choose only 128-bit or higher ciphers for SSL and SFTP protocols. |
|
PCI DSS 4.1 Use strong cryptographic ciphers for transport protocols |
FAILED |
The SSL version is set to auto-negotiable or use SSLv2. You must set the protocol version to SSlv3 and/or TLS only per PCI 4.1 requirements. |
|
PCI DSS 4.1 Use strong cryptographic ciphers for transport protocols |
FAILED |
Unable to ascertain which SSL ciphers were chosen. Select a cipher from the allowed ciphers list instead. |
|
PCI DSS 4.1 Use strong cryptographic ciphers for transport protocols |
FAILED |
One or more MAC algorithms is weak. Choose from hmac-sha1 and hmac-md5 MAC algorithms. |
EFT Server determines whether more than one administrator account has full control over EFT Server. Possible report outcomes include:
|
Requirement |
Status |
Description |
|
PCI DSS 7.1 Limit access to components only to those whose job requires such access |
PASSED |
Only one administrative account exists with full control over EFT Server |
|
PCI DSS 7.1 Limit access to components only to those whose job requires such access |
WARNING |
There is more than one administrator with full control over EFT Server. Ensure that only the minimum level of privileges necessary are granted to administrator accounts |
EFT Server determines whether force password reset is enabled and audits the results.
|
|
When you create a PCI DSS Site that uses LDAP, RADIUS, RSA SecurID® or Windows Active Directory authentication, most password related checks (PCI DSS section 8) are not audited nor reported in the PCI DSS Compliance Report. The report will only indicate that the requirement has passed or failed for EFT Server-managed administrator accounts. |
Possible report outcomes include:
|
Requirement |
Status |
Description |
|
PCI DSS 8.5.3 Users must reset their passwords upon first use |
PASSED |
Password expiration and forced reset is enabled |
|
PCI DSS 8.5.3 Users must reset their passwords upon first use |
FAILED |
Password forced reset is disabled for [Site, Settings Template, Delegated Administrator]. |
|
PCI DSS 8.5.3,9 Allow users to reset their password |
SUCCESS |
You must enable the Allow Password Reset option in order to comply with these requirements. |
EFT Server determines whether the setting to remove user or administrator accounts after 90 days of inactivity option is disabled or set to a value > 90 days (at Admin, Site, Settings Template, user account). EFT Server reports on whether the user account option is set to Disable rather than Remove; and any removal of administrator or user accounts.
Possible report outcomes include:
|
Requirement |
Status |
Description |
|
PCI DSS 8.5.5 Remove or disable inactive user accounts at least every 90 days |
PASSED |
Inactive accounts scheduled to be removed at least every 90 days. |
|
PCI DSS 8.5.5 Remove or disable inactive user accounts at least every 90 days |
WARNING |
The option to disable or expire after <n> days of inactivity for [Site, Settings Template, user, or Administrators] is set to expire. For strict compliance, you should set that option to remove accounts rather than just expire those accounts. |
|
PCI DSS 8.5.5 Remove or disable inactive user accounts at least every 90 days |
FAILED |
The option to remove or disable inactive accounts at least every 90 days is currently disabled for [Site, Settings Template, user, or Administrators]. |
EFT Server determines whether any account has an anonymous password type. Possible report outcomes include:
|
Requirement |
Status |
Description |
|
PCI DSS 8.5.8 Do not use group, shared, or generic accounts and passwords |
PASSED |
No anonymous accounts are present. |
|
PCI DSS 8.5.8 Do not use group, shared, or generic accounts and passwords |
FAILED |
The following account: [username] has an Anonymous type password. You should change this user's password to a normal or One Time Password type to be in compliance with section 8.5.8 of the PCI specification. |
EFT Server determines whether password expiration is enabled and audits the results.
Possible report outcomes include:
|
Requirement |
Status |
Description |
|
PCI DSS 8.5.9 Change user passwords at least every 90 days |
PASSED |
Passwords are set to expire every <n> days. |
|
PCI DSS 8.5.9 Change user passwords at least every 90 days |
FAILED |
Passwords are set to expire after a period of time greater than 90 days (the maximum allowed) for %s, in violation of PCI 8.5.9 |
|
PCI DSS 8.5.9 Change user passwords at least every 90 days |
FAILED |
Passwords are not set to expire for [Site, Settings Template, user, or Administrators]. |
EFT Server determines whether complex password enforcement is enabled, records the value for the minimum password length used, and determines which password character sub-options are enabled.
|
|
Because EFT Server does manage NT/LDAP accounts, when you create a HS-enabled Site that uses LDAP or Windows Active Directory authentication, the Complex Password feature is not available and not audited for the HS Report. The report will indicate that the requirement has passed. |
Possible report outcomes include:
|
Requirement |
Status |
Description |
|
PCI DSS 8.5.10-11 Require a minimum password length |
PASSED |
Password complexity is enabled and properly configured |
|
PCI DSS 8.5.10-11 Use only strong passwords |
PASSED |
Password complexity is enabled and properly configured. |
|
PCI DSS 8.5.10-11 Use only strong passwords |
FAILED |
Enforce complex passwords is disabled for [Site, Settings Template, user, or Administrators]. You must enable complex passwords to meet these requirements. |
|
PCI DSS 8.5.10-11 Use only strong passwords |
FAILED |
Minimum password length is set to less than 7 at [Site, Settings Template, user, or Administrators]. Passwords must be 7 digits or greater to meet PCI 8.5.10 and 8.5.11. |
|
PCI DSS 8.5.10-11 Use only strong passwords |
FAILED |
Require alpha chars and digits for passwords are not for [Site, Settings Template, user, or Administrators]. You must enable those options to comply with PCI 8.5.10 and 8.5.11. |
EFT Server determines whether password history enforcement is enabled for the administrator, Site, Settings Template, and/or a user account.
Possible report outcomes include:
|
Requirement |
Status |
Description |
|
PCI DSS 8.5.12 Disallow reuse of previous passwords |
PASSED |
"Enforce password history" is enabled. |
|
PCI DSS 8.5.12 Disallow reuse of previous passwords |
FAILED |
"Enforce password history" is disabled for [Site, Settings Template, user, or Administrators]. Enable this option to comply with this requirement. |
EFT Server determines whether temporary lockout is enabled or set to a value > 6. Possible report outcomes include:
|
Requirement |
Status |
Description |
|
PCI DSS 8.5.13 Limit repeated access attempts to no more than six |
PASSED |
Temporary lockout duration or account disable is set. |
|
PCI DSS 8.5.13 Limit repeated access attempts to no more than six |
FAILED |
Account lock occurs after <n> invalid attempts. Please set the value to between 1 and 6 to meet PCI DSS 8.5.13 requirements. |
|
PCI DSS 8.5.13 Limit repeated access attempts to no more than six |
FAILED |
Temporary account lockout or disable is disabled for accounts that fail repeated login attempts for Administrators. |
EFT Server determines whether inactivity timeout is enabled, and if enabled, whether it is set to a value that exceeds 15 minutes. Possible report outcomes include:
|
Requirement |
Status |
Description |
|
PCI DSS 8.5.15 Idle sessions should timeout and require login credentials to continue |
PASSED |
Inactivity timeout is enabled and properly configured. |
|
PCI DSS 8.5.15 Idle sessions should timeout and require login credentials to continue |
FAILED |
Inactivity timeout not enabled or set to value exceeding 15 minutes. |
EFT Server determines whether data sanitization is enabled, and if enabled. Possible report outcomes include:
|
Requirement |
Status |
Description |
|
PCI DSS 9.10.2 Destroy electronic media so that cardholder data cannot be reconstructed. |
PASSED |
Data removal sanitization (wiping) is enabled. |
|
PCI DSS 9.10.2 Destroy electronic media so that cardholder data cannot be reconstructed. |
FAILED |
Data sanitization is not enabled. Either enable wiping or make sure you have compensating controls in place to meet this requirement. |
EFT Server determines whether the audit database is connected and properly configured. Possible report outcomes include:
|
Requirement |
Status |
Description |
|
PCI DSS 10.2.3 Implement automated audit trails |
PASSED |
Server's Database Audit is connected. |
|
PCI DSS 10.2.3 Implement automated audit trails |
WARNING |
Server's Database Audit is not connected or is not configured properly |