SSL Certificate-Based Login
EFT supports authentication using SSL certificates for FTPS, and HTTPS, and AS2 connections, rather than password-based login. This is similar to SFTP authentication in which a particular SFTP key is associated with a user account; when the user logs in and provides the key, as long as the keys match, they are allowed to proceed. Unlike SFTP, SSL offers the option to authenticate using both password and certificate rather one or the other.
Normally, when a client supplies an SSL certificate for the SSL handshake (if requested by EFT), EFT determines whether that certificate is in the global trusted list. If the certificate is trusted, EFT completes the process of negotiating a shared secret and then moves on to the authentication stage, requesting a username followed by a password. If the user enters the wrong password (or no password at all), the authentication attempt fails, even though a certificate was found in the trusted store that matched the client’s certificate.
EFT determines whether certificate keys used on EFT are current and reports the status in the PCI DSS Compliance Report. Refer to Possible Compliance Report Outcomes for more information.
With certificate-based authentication, the sequence of steps would be virtually the same. If certificate-based authentication is enabled, and after the client’s username has been provided, but prior to EFT requesting the user’s password, EFT verifies that the public key of the provided certificate matches the certificate in the trusted store that is associated with (mapped to) this particular user’s account. If a match is made, that user is automatically authenticated for that session. If the protocol expects a username/password sequence, EFT always returns TRUE, regardless of the password supplied by the client (whether null or invalid pass).
Compliance with PCI DSS requires that users change their password upon initial login. Because this login method does not use a password, it potentially violates the PCI DSS and is, therefore, not available on Sites defined using the "strict security settings" option.
The procedures below describe how to specify SSL-based logins for Site, Settings Template, and user accounts.
To specify SSL certificate-based logins for the Site
-
Click the Site that you want to configure.
-
In the right pane, click the Connections tab.
-
Refer to Assigning a Certificate for details of configuring SSL.
To specify SSL certificate-based logins for the Settings Template or a User
Do not specify SSL authentication options for accounts that need to send AS2 transfers. EFT’s HTTP/S protocol handler requires a username and password at the outset of HTTP/S-based AS2 transactions.
-
Click the Settings Template or user that you want to configure.
-
In the right pane, click the Connections tab.
-
Select the FTPS (SSL/TLS) check box, if not inherited from the Site, and then click SSL Auth. The SSL Authentication Options dialog box appears.
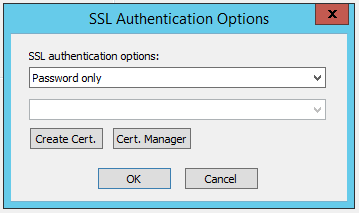
-
In the SSL authentication options list, specify the authentication method:
-
Specified in Settings Template (if the user account is selected)
-
Password only (the default for the Settings Template)
-
SSL Certificate - If SSL Certificate is specified, the bottom box becomes available. Certificates that are defined on the Site appear in the box. Click the user certificate in the box. If no certificate is available:
-
If you need to define a certificate, click Create Cert. The Create SSL Certificate wizard appears.
-
To view or import certificates, click Cert. Manager. The Certificate Manager appears.
-
Click OK to close the dialog box.
-
Click Apply to save the changes on EFT.
Related Topics