Settings screen
Use these settings to allow an Powertech Multi-Factor Authentication administrator to define which authentication methods are authorized, and configure other settings pertaining to Powertech Multi-Factor Authentication's user interactions.
How to Get There
In the Navigation Pane, choose Settings. At least one Authentication Manager must exist before settings can be configured. See Managers screen.
Options
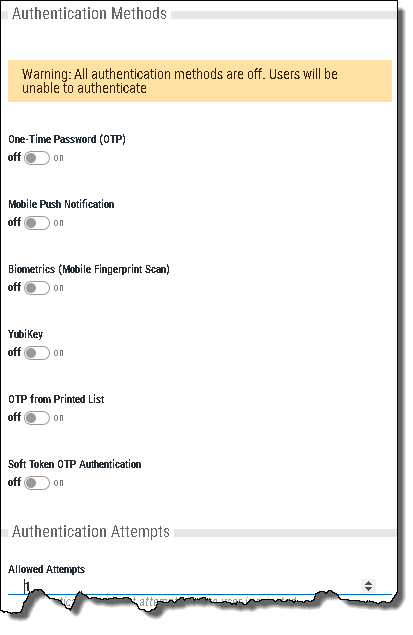
Authentication Methods
Note: When RADIUS authentication is turned on, these settings are unavailable in favor of the RADIUS authentication settings. See RADIUS Authentication screen for more details.
Choose the authentication methods available to network users.
-
One-Time Password (OTP). The Powertech Multi-Factor Authentication agent software prompts the user to enter a one-time password. Network users use their mobile app to generate the one-time password and they enter the value generated . This value is authenticated with the authentication manager.
Note: Powertech Multi-Factor Authentication uses time-based one-time passwords (TOTP) for authentication. If this method is being used, the time on the user’s mobile device must be in sync with the time on the authentication manager server. Time differences of more than one minute will cause validation of TOTPs to fail.
- Mobile Push Notification. A push notification is sent to the network user's mobile app, which displays a notification on-screen. The user is presented with the profile that is attempting to sign in, information about the system that’s being signed into, and a prompt to confirm or deny whether the sign-in attempt is legitimate. If the user confirms that the sign-in attempt is legitimate, a message is returned to the authentication manager to authenticate and the user is allowed to sign in. If the user denies the sign-in attempt, authentication fails and the user is not allowed to sign in. The authentication manager alerts an administrator to a possible hacking attempt.
WARNING: In order for Powertech Multi-Factor Authentication to send Push Notifications to a mobile device outside the private network, the Authentication Manager's Connector Port (port 3040 by default) must be accessible to the public.
- Biometrics (Mobile Fingerprint Scan). This feature is available on mobile devices that contain a fingerprint scanner (e.g. the Google Nexus 5X and 6P, or the iPhone 5S and up). Similar to the push notification processing, a notification is sent to the mobile device prompting the user to authenticate using the fingerprint scanner. If the sign-in attempt is legitimate, the user can authenticate using the fingerprint scanner. If it isn’t, they will have the option to deny the request (as per push notifications).
WARNING: In order for Powertech Multi-Factor Authentication to send Fingerprint Scan prompts to a mobile device outside the private network, the Authentication Manager's Connector Port (port 3040 by default) must be accessible to the public.
- YubiKey. The YubiKey is a FIDO certified U2F USB authentication device that can be used as an alternative to the Powertech Multi-Factor Authentication mobile app. When the Powertech Multi-Factor Authentication agent software prompts for the second factor, the user selects the YubiKey authentication option, inserts the YubiKey into a USB port on their PC/laptop, and presses a button on the YubiKey.
- OTP from Printed List. This is a printed list of one-time passwords, and is a backup authentication method for the user if they lose their smart phone.
- Soft Token OTP Authentication. You can choose to authenticate using a one-time password (OTP) generated by the soft token. The soft token is launched from the desktop agent and is PIN protected. See Desktop Agent.
Authentication Attempts
Allowed Attempts
Enter the number of authentication request attempts can be made before the user is rejected.
Printed Backup OTP Expiration
Backup List Expiration
Enter the number of days a printed list of one-time passwords will be valid.
New User Action
This drop-down menu allows you to configure Powertech Multi-Factor Authentication's authentication settings upon user creation.
When a new user is created:
- Set User to Authenticate Immediately. Require authentication at next user sign on. If you choose this option, new users enrolled in Powertech Multi-Factor Authentication will be required to authenticate using a registered device the first time they sign on. This means they will need to register a device with Powertech Multi-Factor Authentication prior to their next sign on attempt in order to gain access.WARNING: If this option is selected, users will be locked out of the system until they have registered a device with Powertech Multi-Factor Authentication.
- Set User to Authenticate only after Device Registration. Require authentication after user registers a device. If you choose this option, new users enrolled in Powertech Multi-Factor Authentication will not be prompted to authenticate upon sign on until after they have registered a device.
- Manually Set Authentication Option for User. Administrator is responsible for activating or deactivating authentication on an individual user basis using the 'Authenticate User' option in the Edit User settings for each new user (regardless of whether a device has been registered or not).
User Portal
User Portal Session Timeout
Enter the number of minutes an idle User Portal session will remain active before timing out and requiring the user to sign on again.
Log successful User Portal logins in User Portal Log; On • Off
This option allows you to specify whether or not to log successful user portal logins. It is disabled (set to Off) by default. HelpSystems recommends that this option remains off unless audit requirements dictate that successful user portal logins must be logged. Toggle to On to activate logging of successful portal logins.
Log Output
Output to Syslog; On • Off
Set to On in order to log output report data to a syslog server, or Off if you do not wish to log report data to a syslog server.
Output to Syslog
Enter the IP address or DNS name and port of the syslog server you would like to output log data to. (The default syslog port is 514.)
10.60.153.12:514
License Expiry Notification
Enabled
Set Enabled to On to receive a notification when the current license is approaching its expiration date.
If enabled, a service runs once per day at 12 noon to check license expiration and send notifications. A notification is sent to the email address specified if a temporary or subscription license is due to expire within 15 days, or if it has already expired.
The notification email is sent once.
Set Enabled to Off if you do not wish to receive a notification in the circumstances listed above.
Email Address to Notify
If License Expiry Notification is enabled, the expiry notification will be sent to the email address specified here.
Name of Person to Notify
Here you can specify the name of the person to be addressed in the body of the email message.
Purging Report Data
Automatically Purge Report Data
Set this option to On if you would like to enable automatic purging of report data. If enabled, a service runs every day at midnight and deletes from the database all report data older than the number of days specified in the 'Days' Worth of Data to Retain' field.
A record is written into the system event log to record the fact that a purge has run.
Set this option to Off to disable purging. When disabled, no data is deleted from the database.
Disable Inactive Users
Use these options to specify whether user accounts are automatically disabled if the user fails to authenticate within a specific number of days.
Disable Users Who Have Not Authenticated in x Days; Off • On
Toggle to On to disable users who are inactive for the specified number of days. Toggle to Off to disable this feature.
Inactive Days Threshold
Specify the number of days without an authentication to be allowed before users are disabled (1-999).
Email User When Account is Disabled; Off • On
Toggle to On to automatically send an email notification to users who are disabled. Toggle to Off to disable the email notification.
Intrusion Detection, Notification, and Lockdown
Use these settings to automatically disable user accounts that repeatedly fail authentication.
Enabled; Off • On
Toggle to On to activate a maximum number of authentication attempts.
Consecutive Invalid Authentication Attempts to Trigger
Enter the number of consecutive invalid authentication attempts to be allowed of users (1-999). If the user exceeds this threshold an email can be sent to the administrator, or the user account can be disabled, or both (depending on the status of subsequent options).
Notify Administrator on Intrusion Detection/Lockdown; Off • On • Administrator Email Address
Toggle to On to automatically send an email notification to the administrator indicating the user account that has been disabled. Toggle to Off to disable the email notification. In the field provided, specify the administrator's email address to be used for the notification. Email server settings can be configured on the Email screen.
Administrator Email Address
With Intrusion Detection, Notification, and Lockdown Enabled, use the following options to specify the action to be taken in response to a user meeting the maximum number of failed authentication attempts.
Email User on Intrusion Detection/Lockdown; Off • On
Toggle to On to automatically send an email notification to the user indicating their user account that has been disabled. Toggle to Off to disable the user email notification.
Disable User Following Intrusion Detection; Off • On
Toggle to On to disable users who exceed the specified maximum number of authentication attempts. Toggle to Off to disable this feature.
Failover Notifications
Send Notification Email when Failover Occurs; Off • On
Toggle to On to automatically send an email notification to the specified email address upon failover to the secondary server. Toggle to Off to disable the sending of these email notifications.
Email must be configured in Powertech Multi-Factor Authentication to use this feature. See Email Settings.
Email Address to Notify
This is the email address that will be used for server failover notifications