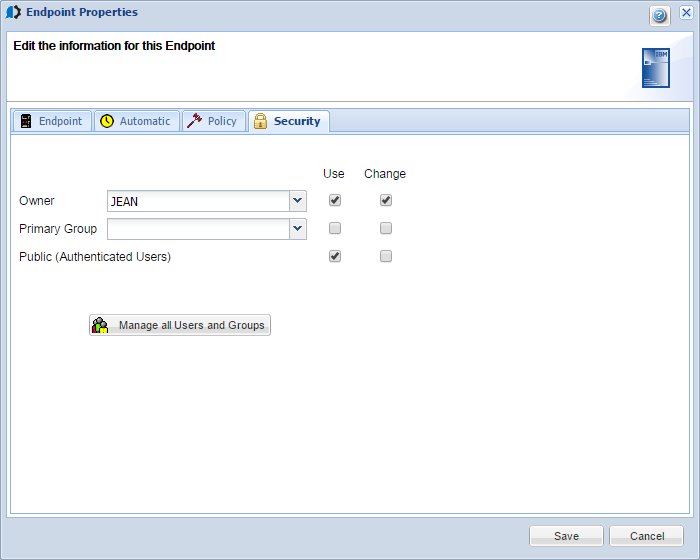
Security tab
Use the Security tab to set security for the Endpoint system.
How to Get There
Right-click an Endpoint system in the System Groups tab, then choose the Security tab.
- Owner: Specifies the Endpoint owner and the owner's authorities. There is only one owner per Endpoint. Selecting a new user name from the drop down menu does not add a new user to an authorization list; instead it changes the Endpoint owner to the selected user. If you want to set authorities and privileges for more than one user, specify a primary group.
- Primary Group: Specifies
an authority group; all users in the group have the same authorities.
You can define users and groups by selecting Manage all Users and
Groups or using the Users and Group Consolidator option.
NOTE: Groups cannot contain other groups; they are simply a list of users.
- Public (Authenticated Users): Specifies the authorities of all users that are approved to use the product.
For each option on the Security tab:
- Use authority allows read-only access to the Endpoint.
- Change authority allows read and write access to the Endpoint. A user with Change authority can modify the properties of the Endpoint.
When checking security, Powertech Compliance Monitor for IBM i checks ownership first. If a user is the owner, the primary group and public authority are not checked. Next, Powertech Compliance Monitor for IBM i checks the group. If a user is part of the primary group, public authority is not checked. Public authority is checked only if the user is not the owner and does not belong to the primary group.
To define or modify the users and groups that can access the Consolidator system, click the Manage all Users and Groups button to display the Authorized Users window.