How to Get There
From the Security Configuration Menu, select option 3.
What it Does
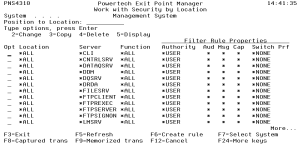
The Work with Security by Location panel allows you to view, create, copy, change, or delete Location Rules.
Options
2=Change
Choose this option for a rule to open the Change Location Rule panel, where you can change a Location Rule.
3=Copy
Choose this option for a rule to open the Copy Location Rule panel, where you can copy a Location.
4=Delete
Choose this option for a rule to delete it.
5=Display
Choose this option to display the Location Rule Derivation panel for the rule.
Field Descriptions
System
System indicates the target of any operations you perform. When you add rules, for example, those rules will be sent to, and will affect processing on, the System named.
Position to Location
Used to position the list.
Opt
Enter a valid option from the list of options provided on the list panel.
Location
Location represents the source of a transaction. Location can hold an IP Address, a Location Group, or the name of an SNA Communications Device.
The special value *ALL, when used on a rule, means that the rule applies to any Location lacking a specific rule. When used as a subset or selection parameter, *ALL generally means to select all such rules for display or printing.
Server
A Server in Exit Point Manager is a controlled entry point into your system. These entry points are determined and defined by IBM. Exit Point Manager has assigned easy-to-remember names to these controlled entry points.
Function
A Function, or Server Function, in Powertech Exit Point Manager for IBM i represents a class of operations that a given Server may perform. For example, the *SIGNON Server classifies its operations as those pertaining to changing passwords, generating authentication tokens, and retrieving signon information. Powertech Exit Point Manager for IBM i has assigned easy-to-remember names to these Functions, such as CHGPWD, GENAUTTKN and RETRIEVE.
Authority
The authority assigned to the location for this server/function.
The possible values are:
Audit
The Audit flag controls the logging of transactions to the Log Journal set up on the Work with Powertech Exit Point Manager for IBM i System Values panel.
The possible values are:
Message
The message property entry will determine if Powertech Exit Point Manager for IBM i sends a message to the specified message queue for the location/server/function.
Capture
Capture transactions for Memorized Transaction Request (MTR).
Switch Profile
The Switch profile entry holds the name of a user profile whose authority is used to process the transaction instead of the authority of the User initiating the transaction. The transaction is executed as, and uses the authority of, this Switch profile. The job that processes the transaction continues to run under this Switch profile until Exit Point Manager processes another transaction request for that job.
Switch profile is allowed only when Authority contains *SWITCH or *MEMSWITCH, if *MEMSWITCH is allowed. Otherwise, it must contain *NONE.
Command Keys
F2 (Global Rule Facility): Maintain rules en mass.
F3 (Exit): Exit the current panel without processing any pending changes.
F5 (Refresh): Refreshes the panel and resets all available text fields.
F6 (Create rule): Creates a new location rule.
F7 (Select System): Use this command key to work with data from a different System.
F8 (Captured trans): Goes to Work with Captured Transaction panel.
F9 (Memorized trans): Goes to Work with Memorized Transaction panel.
F10 (Copy location): Copy all of current location authorities to another location. See Copy rules to another location window.
F12 (Cancel): Exit the current panel without processing any pending changes.
F13 (Display messages): Displays messages for user.
F14 (Work with submitted jobs): Displays jobs submitted from the current job.
F15 (Work with spooled files): Displays the user's print output.
F16 (Sort/subset): Opens the Location Rules Subset panel, which allows you to subset the list of Location Rules by Server, Function, or Location.
F24 (More keys): Displays additional function keys (listed above).