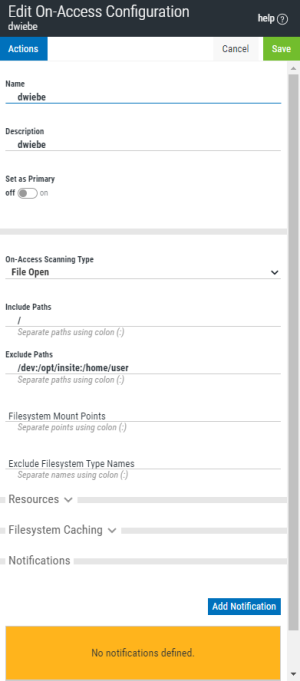
New/Edit/Duplicate On-Access Configuration pane
How to get there
- To create a new Configuration, on the Configurations page, choose Add > On-Access Configuration.
- To create a new Configuration starting with the settings of an existing Configuration, on the Configurations page, for an existing On-Access Configuration, click
 > Properties.
> Properties. - To edit an existing Configuration, on the Configurations page, for an existing On-Access Configuration, click
 > Properties.
> Properties.
What it does
The New/Edit/Duplicate On-Access Configuration pane allows you to set configuration options, including notification settings, for on-access scanning.
Options
Click Actions to open a submenu with the following connection management options:
- Duplicate. Choose this option to duplicate the configuration.
- Delete. Opens the Delete Configuration dialog box, where you are prompted to specify a new Configuration for endpoints assigned to the Configuration you are deleting.
- Close. Choose this option to close the submenu.
Name • Description
The name and description of the configuration.
Set as Primary; Off • On
Endpoints set to the Primary Configuration (see Endpoint Properties pane) inherit the settings of the Configuration that is set as Primary. Toggle this switch to On to indicate that you would like to set endpoints currently assigned to the Primary Configuration to the Configuration you are editing. When you click Save, the number of endpoints that will change is indicated and you are prompted to confirm. Toggle this switch to Off to indicate that you would like to set endpoints assigned to the Primary Configuration to the Default Configuration. The Configuration that is currently set to Primary is indicated in the Configurations page.
On-access scanning Type; File Open • File Open and Closed • Disable
File Open specifies that files should be scanned when users attempt to open the file. File Open and Closed specifies that files should be scanned during file open and after file close. Disable disables on-access scanning.
Include Paths
A colon-delimited list of path names to be included for on-access scanning. A file that exists within any of the path names specified will be subject to scanning unless the file path name is specified as an Exclude Path.
Exclude Paths
A colon-delimited list of path names to be excluded from on-access scanning. The exclude paths take precedence over include paths. A file that exists within any of these path names will not be subject to scanning.
Filesystem Mount Points
This option is for Linux only. A colon-delimited list of mount points for filesystems that are to be monitored for on-access scanning. It provides the means to explicitly set which filesystems will be monitored by fanotify(7). The default is an empty list. Note that filesystems will only be monitored if their type does not appear in the internal list of known unsupported filesystem types and is not part of fsexcl configuration. Note also that the decision to scan a file will still be subject to include and exclude criteria.
Exclude Filesystem Type Names
A colon-delimited list of filesystem type names that are to be excluded from monitoring. The default is an empty list. Note that the decision to scan a file will still be subject to include and exclude criteria.
On Linux, this is used to limit which filesystems will be monitored by fanotify(7), and complements the internal list of filesystem types that we know cannot be monitored. The names are those from the third column of /proc/mounts, see proc(5).
On AIX, the names are those from the first column of /etc/vfs, see vfs(4). The name remote can be used to select all names in /etc/vfs that are marked as remote.
Resources
Thread Allocation
The number of threads to be allocated for use by the on-access scanner. This can be an integer value between 2 and 32. The default is 6. The service must be restarted to change this value.
Max Wait Before Timeout
The maximum amount of time in seconds the scanner should spend scanning a single file or archive before timing out. After the specified number of seconds, the file is allowed to be opened and the file's scan status remains unchanged. This can be an integer value between 0 and 3600. A value of 0 disables the timeout. The default is 300 seconds.
Delay Scan Process
The amount of time in microseconds the scanner should pause with each progress beat from a scanning operation. This can be used as a simple CPU limiting technique for certain use cases. It should not be enabled when operating system files are included in the monitoring paths. This can be an integer value between 0 and 999999. The default value of 0 disables the feature.
Runtime Scheduling Priority
Sets the runtime scheduling priority of the service. This can be a value between -20 (highest priority) and 19 (lowest priority). The default is 0 (no change in priority). The service must be restarted to change this value.
File Clean
Specifies if the engine should attempt to remove the virus from the file. If the file cannot be cleaned, the cleanfail option provides a secondary choice. Set to yes to enable, or no to disable. The default is yes.
File Clean Fail; Quarantine • Delete • No Action
Action if not cleaned. The default is quarantine. Quarantined files are stored under /Quarantined.
Heuristic Analysis
Include heuristic analysis to find new viruses. When you use heuristic analysis the scanning engine employs heuristic technology to detect potentially unknown viruses in executable files (programs). Without this option, the engine can only find viruses that are already known and identified in the current virus definition files. Valid values are yes, no. The default is yes.
Macro
Specifies if you want to treat embedded macros that have code resembling a virus as if they were viruses. This parameter is similar to Heuristic analysis but scans for new viruses in compound document formats; for example, Microsoft OLE formats such as Word documents. Valid values are yes, no. The default is yes.
Programs
Specifies if you want scanning activities to include detection of some widely available applications, such as password crackers or remote access utilities that can be used maliciously or pose a security threat. Valid values are yes, no. The default is no.
Archive Files
Specifies if you want scanning activities to include archive files. Archive files contain embedded files and usually end with one of the following extensions: .ZIP, .TAR, .CAB, .LZH, .JAR and .UUE. This option will also permit scanning of MSCompress files. Valid values are yes, no. The default is no.
File Types; Most Susceptible to Infection • All Files • Examine Files for Known Macro Viruses
Specifies the type of files to include in scanning activities. The default is Most Susceptible to Infection. All Files will scan all files, the slowest option but which provides the best protection. Examine Files for Known Macro Viruses will expand scanning activities to include an examination of files to determine if they contain known macro viruses, faster than the All Files option.
Mime
Specifies if you want to scan inside MIME-encoded files, UU-encoded files, XX-encoded files and BinHex files. The default is Off. Note that to enable this option, the File Types option must be set to all.
Filesystem Caching
Cache
Set to On to enable, or Off to disable the cache. The default is On.
Max Age
A time to live for an unchanged object in the cache. If the object record has not been re-scanned in that time, it will be removed from the cache. This is expressed in minutes, and can be an integer value between 0 and 999999. The default is 0, which disables the feature. Toggle to On to display a text field where you can specify the number of minutes.
Max Idle
A time to live for a cache object that has not been re-scanned (changed) or queried (hit). This is expressed in minutes, and can be an integer value between 0 and 999999. The default is 0, which disables the feature. Toggle to On to display a text field where you can specify the number of minutes.
Max Size
A maximum size for a single filesystem cache. There is one cache per filesystem. The cache expiry operation will reduce the cache to this maximum size, expelling oldest unchanged objects first. This is expressed as the number of files in the cache, and can be an integer value between 0 and 999999999. The default is 0, which disables the feature. Toggle to On to display a text field where you can specify the number of files.
Notifications
Add Notification
Choose this option to open the New/Edit Notification pane, where you can define a new Notification.
 (Show Actions)
(Show Actions)
Select this for a Notification to show a menu with the following options:
- Edit Notification. Opens the New/Edit Notification pane, where you can edit the Notification.
- Remove Notification. Deletes the Notification.
- Close. Choose Close to dismiss the Show Actions menu.