Installation Considerations
Implementation type
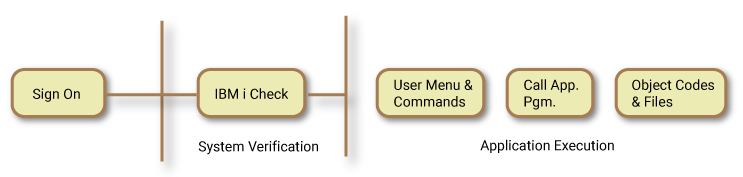
The above diagram shows normal IBM i processing of a sign-on request. The user enters their profile name and password and the IBM i operating system verifies the entries. If the entries are valid, the IBM i passes control to the initial program as specified in the user profile control record. This initial program can be a menu or a program. In normal circumstances, this is most likely to be a menu. The menu allows the user to select the next step of their processing requirement. This is usually the execution of a selected option that then calls an application program. The application program will execute the appropriate object codes and maintain the appropriate database accordingly.
If you use this type of security set up, it will be your responsibility to ensure that the programs, objects, and live data files are properly configured to protect against unauthorized access, unauthorized use of programs, and unauthorized changes of live data. An experienced security officer will know that by using the basic IBM i commands they can fulfil most of the security requirements, but maintaining the integrity of a secured environment can be a major task. Furthermore, the retrieval of pertinent information is not quick enough, meaningful enough, or consolidated in a useful fashion for easy reference.
SecurID is designed to be flexible. It has built in 'switches' to allow you to implement security at your own pace. The more profiles challenged with SecurID authentication, the more secure your environment will be. In the following section, we will discuss how you can introduce SecurID in your system up to the user profile level. This process makes use of DetectIT access control. We call this a 'SIMPLE INSTALLATION'.
Simple installation
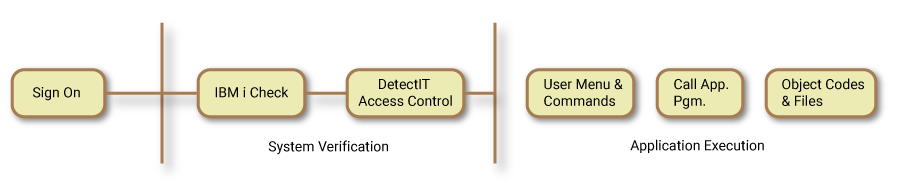
A simple installation allows you to introduce DetectIT access control using SecurID into your IBM i. SecurID complements and enhances existing IBM i facilities. What is more important, it will manage your security more efficiently, with the introduction of integrated and enhanced features over standard IBM i. User profiles can be managed in a controlled manner.
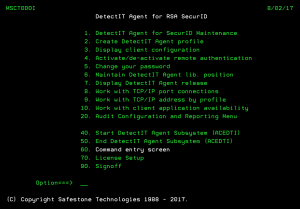
This section refers specifically to programs etc. that can be found on the SecurID master menu (MSCT000I) and the Audit and Reporting menu (MSCT002I). Please acquaint yourself with the programs on these menus before proceeding. You will be required to have the system available when you go through the illustrations below. You will find that program names or commands will be referred to rather than menu option numbers.
Designating a SecurID Security Officer
Profiles to be authorized to administer Powertech RSA SecurID Agent for IBM i must be added to the PTSECURID authorization list. No specific Special Authority values are required as all necessary authority is provided by the appropriate product object owner profiles (PTUSER or PTADMIN).
You can use the following command to add a profile to the PTSECURID authorization list (with *USE authority), where myuser is the administrator profile to add.
ADDAUTLE AUTL(PTSECURID) USER(myuser) AUT(*USE)
Accessing the DetectIT Agent for RSA SecurID menu
The installation places command WRKSECURID into libraries QGPL and @ACE, which can be used to access the DetectIT Agent for RSA SecurID menu, if authorized:
DetectIT Agent for SecurID Maintenance
The function of SecurID is to further enhance the security of the IBM i by imposing SecurID authentication in addition to IBM i authentication.
Activating SecurID authentication
Select the option entitled "DetectIT Agent for SecurID maintenance". When executed, the DetectIt Agent for SecurId Maintenance screen appears, which permits you to perform the following:
- Configure TCP/IP network between IBM i and RSA Authentication Manager server.
- Activate SecurID authentication against any of your profiles.
Other Considerations
The following sections describe the other installation and post installation considerations that you should be aware of so that you can make effective use of this software.
QSECOFR
QSECOFR is the IBM supplied security officer. This profile could easily be misused and therefore the risk associated is extremely high. Access to the password of this profile should be carefully controlled. The password must be authorized by management, and its use should be carefully logged.
It is recommended that the IBM i security officer QSECOFR does not have SecurID authentication activated via SecurID. This will ensure that in the unlikely event that any changes made by IBM to their operating system that may affect QSECOFR, it will not inhibit your ability to work properly as the security officer.
The QSECOFR profile should never be used in the daily running of the computer. The QSECOFR password should be sealed in an envelope and only used in exceptional circumstances. These circumstances may include applying IBM software or SecurID upgrades, changing system values, or controlling object authority. You may even consider introducing dual control or key locks on the QSECOFR password so that there should always be two persons involved in the use of this profile. You should create a substitute security officer adopting the QSECOFR group profile. By doing this, you can still continue to perform with the authority of the security officer and can monitor the activities of QSECOFR. This should rarely happen except when the sealed password is used. Otherwise someone must have breached the security officer's password!
When you are creating the substitute security officer, you should avoid using a name similar to QSECOFR. In this way, you should 'lose' the identity of the new security officer amongst your other users. You should make the name as normal as your other users. The reason behind this is to keep the potential hacker guessing, as surely one of the hacker's main objectives is to retrieve QSECOFR and its password. Since that is not easily available, the next target is to retrieve profiles adopting QSECOFR.
Saving the SecurID Agent
The SecurID libraries and associated Integrated File System (IFS) directory should be backed up on a regular basis as part of your normal operational procedures. The libraries to be saved are as follows:
-@ACE
-@ACE* (Language libraries. The actual library names will depend on the languages that were installed with your SecurID system).
The Integrated File System (IFS) directory to backup is:
/var/ace
The @ACE library contains the most critical data, and should be backed up at least daily.
It is recommended that, where possible, the libraries should be backed up in a dedicated mode:
-Ensure all users using SecurID are signed off.
-Perform Backup.
-Allow users back onto the system.
Where this procedure is not practical, the SecurID libraries can be backed up using other backup functions available within IBM i such as the "save-while-active" technique.
SecurID Agent in the live environment
SecurID offers you a unique facility to determine how you wish to position its libraries within the user's library list. On the relevant menu, there is an option entitled 'Maintain DetectIT Agent lib. position'.
This allows you to define where to place the SecurID libraries: in the system portion or the user's portion of their library list. If the libraries are placed in the system portion, the users cannot change their library list entries using the normal ADDLIBLE or RMVLIBLE or CHGLIBL commands. This is because the CHGSYSLIBL command has a default public authority of *EXCLUDE. Thus, your users can not use this command to change the library in their system portion library list. You could change the authority to allow your users to use this command but that would not be advisable. You should not allow your users to change the system portion of their library lists.
For optimum security, you should place the SecurID libraries in the system portion of the user's library list. This will stop them from removing them from their library list to stop you from monitoring their activities.
Please note the language libraries (@ACE*) must always reside in the system portion of the user's library list. Do not change this entry as it will affect the integrity of the system.
The default setting within the program is *SYSLIBL. This places the SecurID libraries into the user's system portion of their library list.
The following entries are valid:
|
*SYSLIBL |
The SecurID libraries will be added to the system library list of the user. |
|
*USRLIBL |
The SecurID libraries will be added to the user library list. |
|
*NONE |
No library will be added. Libraries will be added using the normal commands. Warning; This method may cause an abnormal functioning of SecurID. |