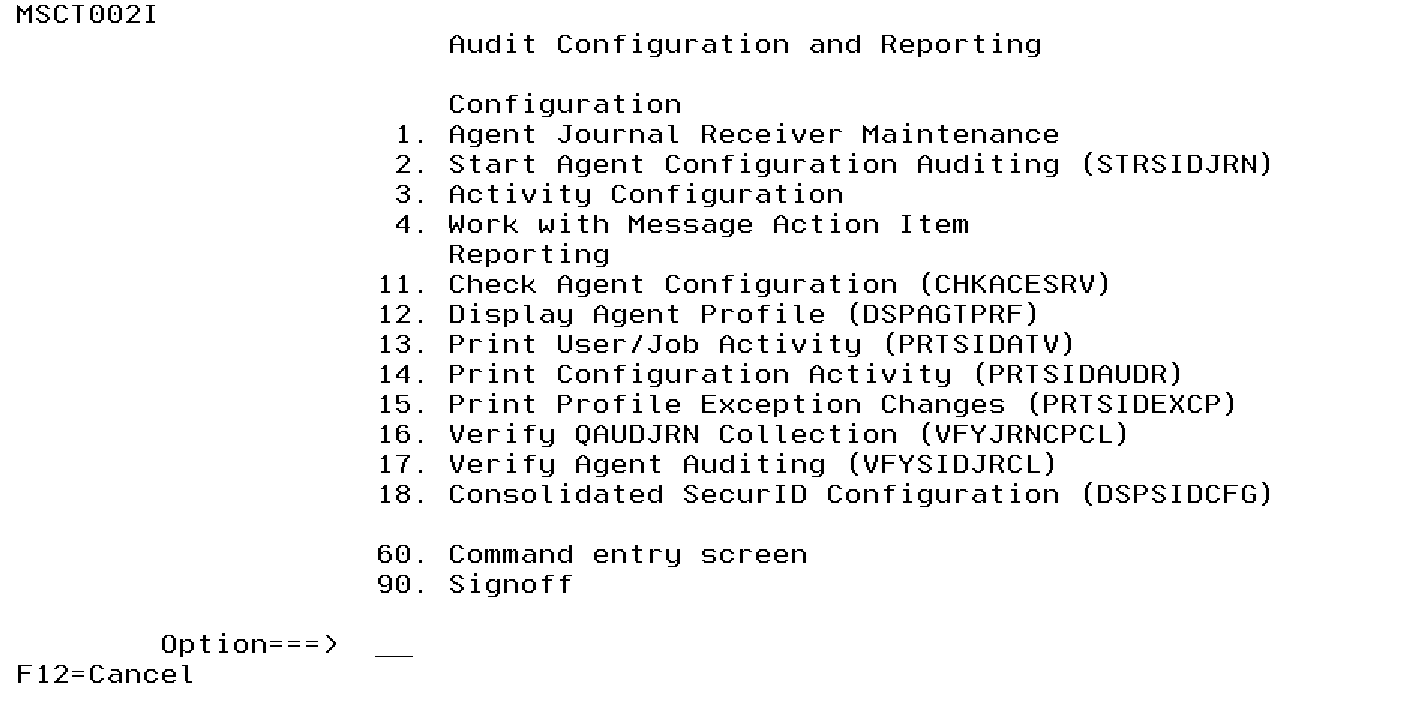
Audit Configuration and Reporting Menu
The following is an overview of the options available on the Audit Configuration and Reporting menu.
How to Get There
From the Master Menu, choose 20.
Options
Option 1. Agent Journal Receiver Maintenance
Select this option to configure the number of days' worth of this software's journal receivers to keep on the system.
With the way IBM i works in relation to receivers, a receiver cannot be deleted without prompting with a message unless that receiver has been "fully saved". Basically, this means to save a receiver it cannot be attached to the associated journal.
This software does NOT save the receivers. Consequently, there is the opportunity for you to save and archive the receivers should you wish to restore and review activity that occurred during a previous time period.
Therefore it is YOUR responsibility to save the journal receivers.
This can be done using the IBM i SAVOBJ command.
There are currently two different journals used by this software:
- Database (file) Activity: The default journal is named 'ACEFILES' and the associated receivers have 'ACE' as the prefix.
- User/Job Activity: The default journal is 'ACEACTJRN' with the associated receivers having a prefix of 'ATV'.
The default journals and receivers are located within the @ACE library.
Option 2. Start Agent Configuration Auditing (STRSIDJRN)
Select this option to activate the audit process for this software.
This is effectively 'all or nothing'. In other words, it will activate the audit processing over all the relevant objects within this software.
Option 3. Activity Configuration
Select this option to configure activity parameters.
The reference to 'activity' means user / job activity. For example, accessing the IBM i system when it is in what is known as 'Restricted State'. For this type of activity to occur, 'Emergency Access' would need to have been activated.
For further details, see Emergency Override Setup.
Option 4. Work with Message Action Item
Select this option to work with Message Action Item.
For further details, see Work with Message Ids.
Option 11. Check Agent Configuration (CHKACESRV)
Select this option to check on the state of the configuration.
The processing looks at the relevant exit points that are accessible via WRKREGINF. Prompting the 'Application Name' on the CHKACESRV command provides a list of those Exit Points that can be reviewed.
Option 12. Display Agent Profile (DSPAGTPRF)
Select this option to review the profiles that have been configured for authentication.
The details are available as a report or within an output file. The name and library for the output file can be specified by the user.
Option 13. Print User/Job Activity (PRTSIDATV)
Select this option to report the User / Job activity based on the configuration settings that had been set within 'Activity Configuration'.
Option 14. Print Configuration Activity (PRTSIDAUDR)
Select this option to report the configuration activity.
Option 15. Print Profile Exception Changes (PRTSIDEXCP)
Select this option to report any changes to User Profiles that would affect authentication.
This is effectively the second of two methods to help prevent users from bypassing the authentication. The process makes use of the IBM i System Audit journal, QAUDJRN. Therefore it is more of an 'after the event' review.
The first and recommended method is to configure the 'Change command exit programs' Exit Point using the option entitled 'Work with client application availability'. This latter option is available on the initial menu that is displayed when signing on via the product administrator profile.
Option 16. Verify QAUDJRN Collection (VFYJRNCPCL)
Select this option to verify the configuration for QAUDJRN.
The use of QAUDJRN is not essential for ensuring users do not bypass authentication. However, if another configuration such as the 'Change command exit programs' Exit Point is no longer making use of a program supplied with this software, QAUDJRN provides a secondary method to review any User Profile changes.
Option 17. Verify Agent Auditing (VFYSIDJRCL)
Select this option to verify the auditing is still in place.
Option 18. Consolidated SecurID Configuration (DSPSIDCFG)
Select this option to check various SecurID configurations and have them output either an outfile or a spool file.
Option 60. Command entry screen
Select this option to access the IBM i Command Entry screen.
Option 90. Signoff
Select this option to end the job that you started on the display station when you signed on.
Function Keys
F12 (Cancel): Cancel and return to the previous point before this menu had been displayed.