Add a New User Accounts Policy Template screen
If you are modifying an existing User Accounts Policy Template, the title of this screen is "Modify template [template name]." This screen allows you to define a User Accounts Policy template, or modify an existing one.
How to get there
On the Manage Servers screen, click  for the server whose policy you would like to add or modify. From the Servers and Policies screen, choose the User Accounts category and click New. Or to modify an existing template, click the template.
for the server whose policy you would like to add or modify. From the Servers and Policies screen, choose the User Accounts category and click New. Or to modify an existing template, click the template.
What it Does
Use these options to add a new User Accounts Policy Template for the selected server.
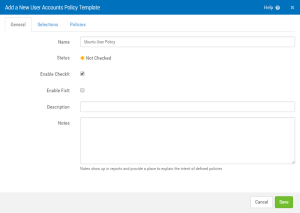
General tab
Name
The name of the policy template.
Status
Lists whether the server is Not checked  , Not Compliant
, Not Compliant  , or Compliant
, or Compliant  .
.
Checked On
Lists the date and time this template was most recently checked.
Enable CheckIt
Check this box to allow Security Auditor to check this value on the server to determine its status.
Enable FixIt
Check this box to allow Security Auditor to fix this value on the server (i.e. change it to match the template value).
Description
This is the template description.
Notes
Enter notes here. Notes show up in reports and provide a place to explain the intent of defined policies.
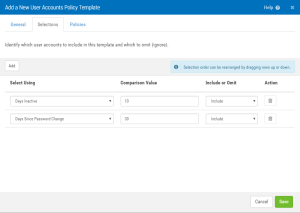
Selections tab
Use these options to identify which user accounts to include in this template and which to omit (ignore).
Add
Click this button to add additional user account selection criteria. A new row is added to the section below. The new criteria will be additive to the existing criteria, and not restrictive. In other words, each row defines a new criteria for users to be included or omitted in the selection. (The rows represent an 'or' and not an 'and' relationship.)
Select Using
Use this list to choose what criteria you would like to use to select the user account.
Comparison Value
Enter the value to compare with the criteria selected (e.g. the user logon name you want to include).
- User Logon Name • Primary Group • Group Member. The user name can be specified exactly or using standard 'glob' characters {*, ?, [],}. Also the '!' character can be placed before the comparison value to get all users that don‘t match.
- Days Inactive. Users who have not logged on in more days than the comparison value will be selected.
- Days Since Password Change. Users who have not changed their password in more days than the comparison value will be selected.
- UID • No Password • Non Unique UID. Integer values can be a single value, a set of values, a range or a set of ranges and values. A set of acceptable values are separated by the character ';' like 1;7;11. A range of acceptable values are separated by a ':' like 1:20. If an endpoint is missing (e.g. 500:) it implies all numbers less than or greater than the specified endpoint. A set of ranges and values are separated by both ';' and ':' like 1:20;25;30:35.
Include or Omit
Choose whether you want to include or omit user accounts that match this criteria.
Action
Select  (Remove) to delete the policy item, respectively.
(Remove) to delete the policy item, respectively.
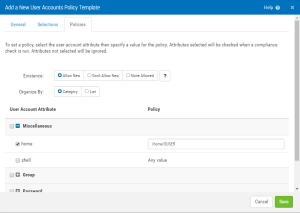
Policies tab
Use the options on this tab to define your Policy. To set a policy, select the user account attribute then specify a value for the policy. Attributes selected will be checked when a compliance check is run. Attributes not selected will be ignored.
Existence: Allow New • Don't Allow New • None Allowed
If 'Allow New' then new instances of the user accounts selected will not be identified as out of compliance. If 'Don't Allow New' then new instances of the user accounts selected that are not in the baseline will be identified as out of compliance. (The baseline is created when the first compliance check (CheckIt) is run. Non-compliant (new) users can be accepted into the baseline after subsequent checks.) If 'None Allowed', any user accounts discovered on a compliance check are non-compliant.
Organize By: Category • List
Use these buttons to select how you would like to organize the attributes.
Linux User Account Attributes (Ubuntu, RHEL, CentOS, Oracle, SLES)
home
Full path name of the home directory of the user. The $USER macro can be used for defining policy, e.g. /home/$USER.
shell
Defines the program run for the user at session initiation - full path name.
pgrp
Identifies the users primary group - value cannot be null. The $USER macro can be used for defining policy, e.g. $USER.
groups
Identifies the groups the user belongs to. The $USER macro can be used for defining policy, e.g. $USER group2 group3.
pass_max_days
The maximum number of days a password may be used. If the password is older than this, a password change will be forced. If not specified, -1 will be assumed (which disables the restriction).
pass_min_days
The minimum number of days allowed between password changes. Any password changes attempted sooner than this will be rejected. if not specified, -1 will be assumed (which disables the restriction).
pass_warn_age
The number of days warning given before a password expires. A zero means warning is given only upon the day of expiration, a negative value means no warning is given. If not specified, no warning will be provided.
account_expires
Set the date or number of days since January 1, 1970 on which the users account will no longer be accessible. The date may also be expressed in the format WW-MM-DD (or the format more commonly used in your area). A user whose account is locked must contact the system administrator before being able to use the system again. Note that an account expiration differs from a password expiration. In case of an acount expiration, the user shall not be allowed to login. In case of a password expiration, the user is not allowed to login using her password.
inactive
The number of days after password expires that account is disabled.
pass_locked
Indicates if the user account is locked. This is indicated in the shadow password file by a prefix before the encrypted password. A user with password locked may still login through other mechanisms such as a ssh key.
AIX User Account Attributes
admin
Defines the administrative status of the user. Possible values are: (1) true - The user is an administrator. Only the root user can change the attributes of users defined as administrators. (2) false - The user is not an administrator. This is the default value.
admgroups
Lists the groups the user administrates. The value parameter is a comma-separated list of group names.
auth1
Primary auth method (Deprecated: use SYSTEM). Lists the primary methods for authenticating the user.
auth2
Lists the secondary methods for authenticating the user.
SYSTEM
Defines the system authentication mechanism for the user.
capabilities
Defines the system privileges (capabilities) which are granted to a user by the login or su commands. The Value parameter is a list of comma-separated classes.
default_roles
Specifies the default roles for the user; can only contain roles assigned to the user in the roles attribute. You can use the ALL keyword to signify that the default roles for the user are all their assigned roles. The Value parameter is a list of comma-separated classes.
home
Full path name of the home directory of the user. The $USER macro can be used for defining policy, e.g. /home/$USER.
rcmds
Controls the remote execution of the r-commands (rsh, rexec, rcp); Possible values are allow (default), deny, and hostlogincontrol, which specifies that the ability of remote command execution is determined by the hostsallowedlogin and hostsdeniedlogin attributes. The user is only allowed to execute remote commands on a target system if the user (or target user) is allowed to log in the target system.
roles
Lists the administrative roles for this user. The Value parameter is a list of role names, separated by commas.
shell
Defines the program run for the use: at session initiation - full path name.
su
Indicates whether another user can switch to the specified user account with the su command - true (default) or false.
sugroups
Lists the groups that can use the su command to switch to the specified user account a value of ALL indicates all groups. An ! (exclamation point) in front of a group name excludes that group. If this attribute is not specified, all groups can switch to this user account with the su command
unmask
Determines file permissions at time of creation; the default is 022.
auditclasses
Lists the users audit classes. The Value parameter is a list of comma-separated classes, or a value of ALL to indicate all audit classes.
pgrp
Identifies the users primary group - value cannot be null. The $USER macro can be used for defining policy, e.g. $USER.
groups
Identifies the groups the user belongs to. The $USER macro can be used for defining policy, e.g. $USER group2 group3.
dictionlist
Defines the password dictionaries used when creating new passwords.
histexpire
Defines the period of time (in weeks) that a user cannot reuse a password. The value is a decimal integer string. The default is 0, indicating that no time limit is set. Only an administrative user can change this attribute.
histsize
Defines the number of previous passwords a user cannot reuse. The value is a decimal integer string. The default is 0. Only an administrative user can change this attribute.
maxage
Defines the maximum age in weeks of a password. The password must be changed by this time. The value is a decimal integer string. The default is a value of 0, indicating no maximum age. Range: 0 to 52
maxexpired
Defines the maximum time in weeks beyond maxage that a user can change an expired password. After this defined time, only an administrative user can change the password. The value is a decimal integer string. The default is -1, which means the user can always change their expired password regardless of how many weeks have passed. If the maxexpired attribute is 0, the password expires when the maxage value is met. If the maxage attribute is 0, the maxexpired attribute is ignored. Range: 0 to 52 (a root user is exempt from maxexpired)
maxrepeats
Defines the maximum number of times a character can be repeated in a new password. Since a value of 0 is meaningless, the default value of 8 indicates that there is no maximum number. The value is a decimal integer string. Ranqe: 0 to 8
minage
Defines the minimum age (in weeks) a password must be before it can be changed. The value is a decimal integer string. The default is a value of 0, indicating no minimum age. Range: 0 to 52
minalpha
Defines the minimum number of alphabetic characters that must be in a new password. The value is a decimal integer string. The default is a value of 0, indicating no minimum number. Range: 0 to 8
mindiff
Defines the minimum number of characters required in a new password that were not in the old password. The value is a decimal integer string. The default is a value of 0, indicating no minimum number. Range: 0 to 8
minlen
Defines the minimum length of a password. The value is a decimal integer string. The default is a value of 0, indicating no minimum length. The maximum value allowed is 8. This attribute is determined by minlen and/or minalpha + minother, whichever is greater. minalpha + minother should never be greater than 8. If minalpha + minother is greater than 8, then the effective value for minother is reduced to 8 - minalpha.
minother
Defines the minimum number of non-alphabetic characters that must be in a new password. The value is a decimal integer string. The default is a value of 0, indicating no minimum number. Range: 0 to 8
pwdchecks
Defines the password restriction methods enforced on new passwords. The value is a list of comma-separated method names and is evaluated from left to right. A method name is either an absolute path name or a path name relative to /usr/lib of an executable load module.
pwdwarntime
Defines the number of days before the system issues a warning that a password change is required. The value is a decimal integer string. A zero or negative value indicates that no message is issued. The value must be less than the difference of the maxage and minage attributes. Values greater than this difference are ignored and a message is issued when the minage value is reached.
account_locked
Indicates if the user account is locked - yes, true, and always are equivalent no, false, and never are equivalent.
expires
Identifies the expiration date of the account. The Value parameter is a 10-character string in the MMDDhhmmYY form, where MM = month, DD = day, hh = hour, mm = minute, and YY = last 2 digits of the years 1939 through 2038. All characters are numeric. If the Value parameter is 0, the account does not expire. The default is 0.
login
Indicates if the user can log into the system with the login command - true (default) or false.
loginretries
Defines the number of unsuccessful login attempts allowed after the last successful login before the system locks the account. A zero or negative value indicate that no limit exists.
maxulogs
Defines the maximum number of logins for the user. If the concurrent login number for a user exceeds the maximum number of allowed logins, the login is denied.
rlogin
Indicates if the user can access the account remotely with the telnet or rlogin commands - true (default) or false.
Windows User Account Attributes
Home Directory
The home directory of the user. The $USER macro can be used for defining policy, e.g. /home/$USER.
groups
The list of groups that the user is a member of. The policy value is a comma separated list of group names. The $USER macro is supported.
User May Change Password
Can the user change the password?
Password Expired *
Has the password expired?
Password Expires *
Does the password expire?
Password Expiration Date *
The Password Expiration Date. The policy value can be the expiration timestamp [yyyy-mm-dd hh:mm:ss], the expiration day [yyyy-mm-dd], expires within x days [number], expires during days range [number:number], or no expiration [blank].
Password Required
Is a password required to log on?
Account Expired *
Has the account expired?
Account Expires *
Does the account expire?
Account Expiration Date
The account expiration date. The policy value can be the expiration timestamp [yyyy-mm-dd hh:mm:ss], the expiration day [yyyy-mm-dd], expires within x days [number], expires during days range [number:number], or no expiration [blank]. FixIt only supports expiration day or no expiration [blank].
Account Active
Is the account active? The policy value can be yes, no, or locked. FixIt only supports yes or no.
Logon Script
The logon script for the user. $USER macro is supported.
Profile Path
The profile path to the user account. $USER macro is supported.
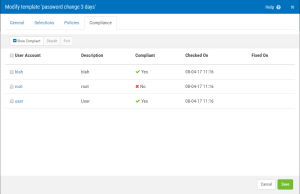
Compliance tab
This tab appears if CheckIt results exist, and shows the status of user accounts that have been checked.
Show Compliant
Check this box to show compliant records.
CheckIt
Use this button to run CheckIt, which performs a compliance check for the selected files.
Cancel • Save
Click Cancel to dismiss this screen without making changes. Click Save to save changes.