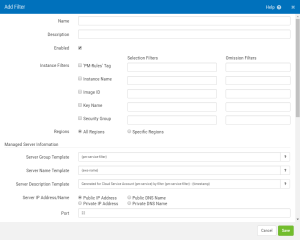
Add/Edit Filter
How to Get There
Create a new Cloud Service Account in the Manage AWS Cloud Service Accounts screen. Click  (Edit Filters).
(Edit Filters).
What it Does
Security Auditor uses the Filter settings to create Managed Servers for the discovered instances automatically.
Options
Name
The name of the Filter. Since a Filter can only add servers to a single group, and a group must contain instances of the same Linux distribution, consider including the distribution in the name of the filter.
Description
The description of the Filter.
Enabled
Check this box to use the Filter settings to create Managed Servers.
Instance Filters; Selection Filters • Omission Filters
Filters allow you to identify the server instances you would like to add automatically during polling. Use the Selection Filters column to identify the server instance to add, and the Omission Filters column to identify the server instances to omit. For each enabled filter attribute, the Selection filters are processed first, then the Omission filters remove omitted instances from the results. When multiple filter attributes are selected, only server instances that match every enabled attribute filter are selected. Instances are selected or omitted when any one of the selection/omission values are met.
Use the following to help specify server instances by Instance Name, Image Name, Key Name, and Security Group:
- Select all instances with * (asterisk).
- Use * as a wildcard character (StartsWith*).
- Separate multiple values with a comma (StartsWithA*, *EndsWithB, *ContainsC*).
Use the following to help specify server instances by Tag:
- The Tag Filter format is TagKey=TagValue.
- Select all instances with TagKey=*.
- Supports * (any string) and ? (any character) wildcards and multiple comma separated selections (TagA=StartsWithA*, TagB=*EndWithB,TagC=*ContainsC*).
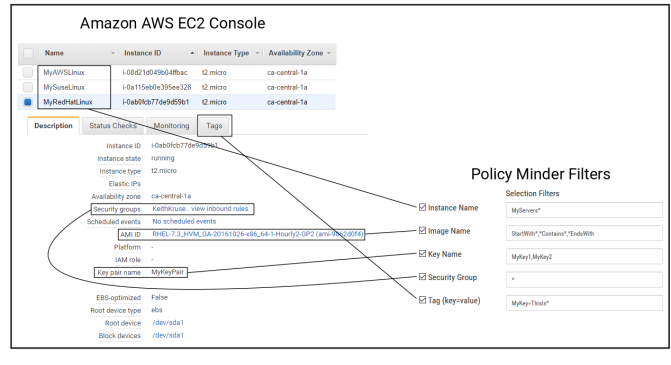
- Instance Name. Use this field to identify server instances by the Name of the AWS instance, if defined. If no Name is defined, and a value is entered here, Security Auditor looks for the Instance ID.
- Image Name. Use this field to identify server instances by the Image Name. In Amazon AWS, this is listed as the AMI ID.
- Key Name. Use this field to identify server instances by the Key Pair Name.
- Security Group. The Security Group assigned to the instance.
- Tag (key=value). Use this field to identify server instances with Tags.
Regions; All Regions • Specific Regions
Choose All Regions to perform the filter comparison for all Amazon AWS server regions. Choose Specific Regions to identify the regions to perform the filter comparison. Choose the minimum number of required regions for optimal performance.
Managed Server Information
Server Group Template
The name of the Server Group that discovered servers will be assigned to. Aim to include servers that share policies in the same Group in order to reduce the number of policies that must be defined. Supports the following variables:
- {aws-key}
- {aws-security-group}
- {pm-service}
- {pm-service-filter}
- {os}
Server Name Template
The unique name of the Managed Servers created for discovered servers. Supports the following variables:
- 'Server Group Template' variables
- {server-group}
- {aws-name}
- {aws-instance-id}
- {aws-private-ip}
- {aws-public-ip}
- {aws-public-dns}
- {aws-private-dns}
- {host-name}
Server Description Template
The Description of the Managed Servers created for discovered servers. Supports the following variables:
- 'Server Name Template' variables
- {server-name}
- {date}
- {time}
- {timestamp}
Server IP Address/Name; Public IP Address • Public DNS Name • Private IP Address • Private DNS Name
Specify whether the managed server uses a Public/Private IP Address/DNS Name.
Port
The ssh port - default is port 22. (Unix-based servers.)
Installation Connection Information
Installation Connection Information is needed to initially access the server to configure future connections (See 'Installation Configuration' below). The servers are accessed using this information only when the server is initially added as a Managed Server.
Installation User Name
The user name used for installation.
Authenticate With; Password • Managed Key
Choose Password and enter the password if you are using a password for authentication.
Choose Managed Key to select an existing Managed Key. Managed Private Keys are created and managed using Admin Tasks > Manage Private Keys. See Manage Private Keys.
Elevate Permission With; sudo • su • Do Not Elevate
Use this drop-down to specify whether or not you would like to elevate permissions, and the method for doing so (sudo or su).
Authorization Password
This is the password required to elevate permissions. If no password is required this field may be left blank.
Installation Configuration
Installation will create the user and group below, create public/private key pair allowing the Security Auditor console ssh access as that user, and update the sudo configuration to allow that user authority to perform commands required for Security Auditor's agentless access.
Security Auditor User • Specify UID
A user with this name will be created on the managed server and used by Security Auditor for agentless control.
Security Auditor Group • Specify GID
A group with this name will be created on the managed server and used by Security Auditor for agentless control.
sudoers file • Use sudoers d
Enter the path to the sudoers file where sudo config is located. If 'Use sudoers.d' is checked then the necessary sudoers additions for the Security Auditor user to execute commands via sudo will be placed in a new file in the sudoers.d directory (this is a best practice). If unchecked then the necessary changes will be appended to the sudoers file.
Cancel • Save
Choose Cancel to dismiss the screen without saving changes. Choose Save to save changes and return to the Manage Filters screen.