Add/Modify Files Template screen
If you are modifying an existing Files Policy Template, the title of this screen is "Modify template [template name]." This screen allows you to define a Files Policy template, or modify an existing one.
How to get there
On the Manage Servers screen, click  for the server whose policy you would like to add or modify. Or, from the Servers and Policies screen, choose the Scripts category and click New, or to modify an existing template, click the template.
for the server whose policy you would like to add or modify. Or, from the Servers and Policies screen, choose the Scripts category and click New, or to modify an existing template, click the template.
What it Does
Use these options to add or modify a Files Policy Template.
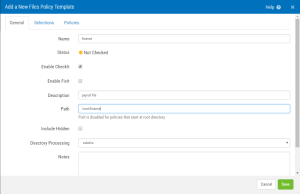
General tab
Name
The name of the Files Policy template.
Status
The status of the Files Policy template. Not checked  , Not Compliant
, Not Compliant  , or Compliant
, or Compliant  .
.
Checked On
Lists the date and time this policy was last checked (modify only)
Enable CheckIt
Check this box to allow Security Auditor to check this value on the server to determine its status.
Enable FixIt
Check this box to allow Security Auditor to fix this value on the server (i.e. change it to match the template value).
Description
A description of the file.
Path
The path of the file on the server. Fixlt is disabled for policies that start at root directory.
Include Hidden
Check this box to include hidden files in the policy.
Directory Processing
Choose 'subdirs' to include subdirectories. Choose 'noSubDirs' to omit suibdirectories. Choose specifyMinMaxDepth to indicate the minimum and maximum directory depth.
- Minimum Depth: Do not apply any tests or actions at levels less than n (a non-negative integer). -mindepth 1 means process all files except the starting-points.
- Maximum Depth: Descend at most n levels (a non-negative integer) of directories below the starting-points. -maxdepth 0 means only apply the tests and actions to the starting-points themselves.
Notes
Enter notes here. Notes show up in reports and provide a place to explain the intent of defined policies.
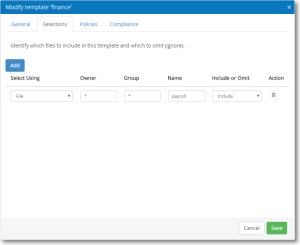
Selections tab
Use this tab to identify which files to include in this Template and which to omit (ignore).
Add
Click Add to add an additional user account.
Select Using
Use this list to choose what criteria you would like to use for selection: file, directory, attributes, files with no owner, files with no group, directories with no owner, or directories with no group.
Owner • Group • Name
Unix glob characters allowed: *= one or more chars, ?=a single char, [xyz]=a char from set, [!xyz]=a char not from set. Also the '!' operator (e.g. !staff) preceding the pattern means anything other than the pattern specified.
Include or Omit
Choose whether you want to include or omit this criteria.
Action
Select  (Remove) to delete the policy item, respectively.
(Remove) to delete the policy item, respectively.
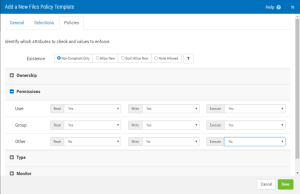
Policies tab
Use this tab to identify which attributes to check and values to enforce.
Existence: Non-Compliant Only • Allow New • Don't Allow New • None Allowed
If 'Allow New' then new instances of the user accounts selected will not be identified as out of compliance. If 'Don't Allow New' then new instances of the user accounts selected that are not in the baseline will be identified as out of compliance. (The baseline is created when the first compliance check (CheckIt) is run. Non-compliant (new) users can be accepted into the baseline after subsequent checks.) If 'None Allowed', any user accounts discovered on a compliance check are non-compliant.
Ownership • Attributes • Permissions • Extended Permissions • Type • Monitor
Here, specify policy criteria for file ownership, attributes, permissions, extended permissions, type, and specify what to monitor. The categories available here depend on the operating system of the server.
Attributes (Windows):
- Archive: A file or directory that is an archive file or directory. Applications typically use this attribute to mark files for backup or removal.
- Compressed*: A file or directory that is compressed. For a file, all of the data in the file is compressed. For a directory, compression is the default for newly created files and subdirectories.
- Encrypted*: A file or directory that is encrypted. For a file, all data streams in the file are encrypted. For a directory, encryption is the default for newly created files and subdirectories.
- Hidden: The file or directory is hidden. It is not included in an ordinary directory listing.
- NotContentIndexed: The file or directory is not to be indexed by the content indexing service.
- ReadOnly: A file that is read-only. Applications can read the file, but cannot write to it or delete it. This attribute is not honored on directories.
- System: A file or directory that the operating system uses a part of, or uses exclusively.
Type:
- SUID: SUID on an executable file means that when the file is executed, the process runs with an effective UID of the owner of the file. The SUID is not supported on shell scripts, and it has no meaning on a directory.
- SGID: SGID on an executable file means that when the file is executed, the process runs with an effective GID of the group owner of the file. The SGID on a directory means that any file or directory created within the directory will have the same group ownership as the directory, rather than of the primary group of the user. The SGID permission bits are propagated down through the directory structure, so any directory created within a directory with the SGID bit set also inherits that bit.
- SVTX: SVTX on a directory means that even if the directory has global write permission (such as /tmp), users cannot delete a file in the directory unless they own the file or the directory.
The format for the “Specify”, “Deny”, and “Permit” values of Extended Permissions (AIX) are:
- One or more “mode strings” separated by an “&” character.
- A “mode string” has two parts separated by a space:
- Three character “rwx” mode. (Hyphen replaces unspecified permission)
Examples:
rwx = Read, Write, and Execute
r-- = Read
-wx = Write and Execute
- User/Group Info String:
- User string example:
u:username
- Group string example:
g:groupname
- User string example:
- Three character “rwx” mode. (Hyphen replaces unspecified permission)
Complete “mode string” examples:
rwx u:user1 = Read, Write, and Execute authority to User “user1”
--x g:group1 = Execute authority to Group “group1”
- Examples of complete policy strings for “Specify”, “Deny”, and “Permit” attributes are:
r-- u:user1
--x g:group1
rwx u:user1&--x g:group1&rw- g:group2
rwx u:user1& rwx u:user2& rwx u:user3
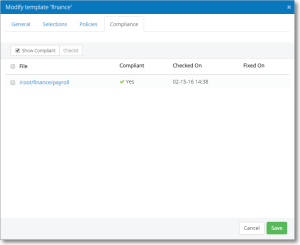
Compliance tab
Use this tab to view and check existing Files Policies.
Show Compliant
Check this box to show compliant files.
CheckIt
Use this button to run CheckIt, which performs a compliance check for the selected files.
Cancel • Save
Click Cancel to dismiss this screen without making changes. Click Save to add or save changes to the Policy Template.