User Accounts
Security Auditor supports User Account policies for AIX, Linux, and Windows servers.
What user account attributes need to be checked and the requirements for user profile compliance will vary from organization to organization. Some of the common user account templates we see configured are used to check for:
- New admin accounts
- Inactive accounts
- Members of a particular group to be configured with specific settings such as logon and audit settings.
- Accounts with UID of 0 (other than root)
- Multiple accounts with the same UID
Example – Detecting New Admin Accounts on AIX
The following steps are essentially the same regardless of the platform of the server being managed.
Defining the template
- To get to the User Account category, on the Manage Servers screen, click the
 category for the Private or Group Policy in the row of the desired server.
category for the Private or Group Policy in the row of the desired server. - Click New. The Add a New User Accounts Policy Template screen appears.
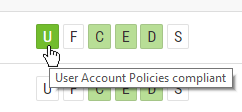
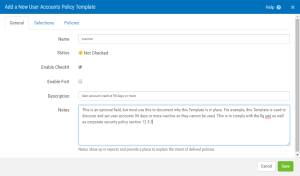
- Fill out the General tab – example below.
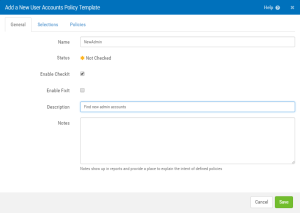
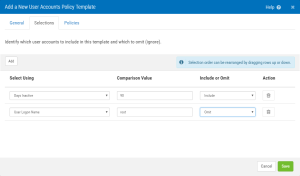
- Click on the Selections tab, then click on Add to choose the user accounts that will be examined during a compliance check. For this example we’re selecting Admin but you can select users based on, for example:
- User account name (using the full name or a generic (as in bob*))
- Accounts that have a specific primary group
- Members of a specific group
- Number of days the account has been inactive
- Number of days since the last password change
- UID (to check for accounts with UID of 0 – in addition to root, for example)
- Non-unique UIDs
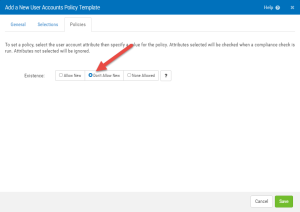
- Click on the Policies tab. This is where you specify what user account attributes will be checked when a compliance check is run. For this example, we’re not going to select any user account attributes. Rather, we are going to disallow new accounts. To do so, select the Don't Allow New radio button.
- Click Save.
Or go to Servers and Policies > [server name]. In the drop-down lists, select whether this should be a Private or Group Policy, then select User Accounts.
The first time a compliance check is run on this template, a baseline of all of the current admin accounts is established. On subsequent compliance checks, if new admin accounts are created or accounts are changed to be an admin, the compliance check will identify any account not in the baseline as out of compliance.
To run a compliance check, do one of the following
- On the Manage Servers screen, click
 next to a server to open the server's Files policies.
next to a server to open the server's Files policies.- Click
 for the Template under the Action column. Or,
for the Template under the Action column. Or, - Select one or more Templates and click CheckIt. This will run a compliance check on all the selected user account Templates.
- Click
- Choose Servers > CheckIt. Choose the server from the Servers tab and then user account Templates from the Policies tab, then click CheckIt.
- Schedule a regular compliance check. Go to Admin tasks > Manage Scheduled Jobs.
The first time a compliance check is run on this template all accounts will be in compliance.
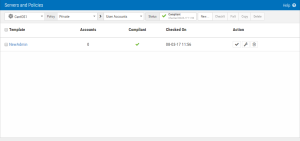
If the template is out of compliance, then a new admin account has been discovered. Click on the template name and then the Compliance tab to determine the new admin account name. In the example below, the Show Compliant box has been unchecked to only show the non-compliant accounts. In this case, the markj account is out of compliance.
If you click on the user account name, you’ll see that the account is out of compliance because it’s New. Some organizations grant admin rights to individuals temporarily for a special project. Leaving the account out of compliance will serve as a reminder to remove the admin rights once the project is complete.
The ‘Allow new accounts’ policy attribute is not limited to finding new admin accounts. You can use the ‘Allow new accounts’ for other templates - perhaps to track new members of a particular group.
Example – Managing Inactive Accounts
Ensuring user accounts are unable to be used when they are no longer active is both a good security practice as well as required by many laws and regulations. Let’s see how you can automate this process:
Define the template
- To get to the User Account category, on the Manage Servers screen, click the
 category for the Private or Group Policy in the row of the desired server.
category for the Private or Group Policy in the row of the desired server. - Click New. The Add a New User Accounts Policy Template screen appears.
- Fill in the General tab – see below:
- Click on the Selections tab, click Add, and then click on the drop down and choose Days Inactive.
- Enter the number of days inactive you want to select on.
- Click Add if you want to, for example, omit any accounts from being examined during the compliance check.
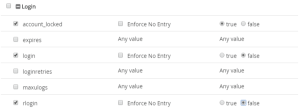
- Click the Policies tab. In this example we’ve opened up the Login category so that we can specify what the values should be for the account_locked, login and rlogin attributes. These will be compared to the user account settings during a compliance check. Notice the “Enforce No Entry” field in the middle column. There are times, when you want to force values to come from the user account global settings – for example, you typically want this to occur for the password attributes so that you can manage password composition rules on a global basis, rather than an individual basis. But in this case, we don’t want these settings to come from the global value. We actually want them to be set in the entry for the inactive user accounts.
- Click Save.
Or, go to Servers and Policies > [server name]. In the drop-down lists, select whether this should be a Private or Group Policy, then select User Accounts.
Run a compliance check
When you run a compliance check on this template any user account inactive 90 days or more will be examined. The accountlocked attribute must be true and login and rlogin must be false. If any attributes do not match these rules, the user account will be identified as out of compliance.
To run a compliance check, do one of the following:
- Click
 next to the template name and then click CheckIt.
next to the template name and then click CheckIt. - Go to Servers > CheckIt, choose the server. NOTE: This runs a compliance check against all templates in the User account category.
- Create a cron job to run the compliance check. Go to Admin tasks > Manage Scheduled Jobs (creating scheduled jobs is discussed later).
If the template is out of compliance (indicated by a  in the Compliant column), click on the template name and then the Compliance tab to determine the accounts out of compliance. Click on the account name to see the details of why it’s out of compliance.
in the Compliant column), click on the template name and then the Compliance tab to determine the accounts out of compliance. Click on the account name to see the details of why it’s out of compliance.
Run FixIt
FixIt changes the settings of the user account to match the policy (as defined by the template.) To run FixIt, you must first enable it for this template. To enable FixIt, click on the template name then, on the General tab, check the Enable FixIt box. Once you have enabled FixIt, you can run it on the individual user account that is out of compliance or run it on the entire category by selecting the user or template and clicking the FixIt button.
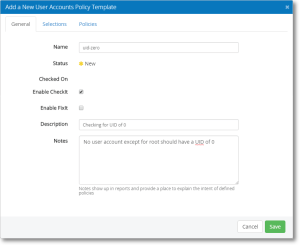
Example – Checking for UID of 0
Making sure there are no other user accounts besides root with UID of 0 is a routine request of many auditors. Here’s how you’d configure that template:
Define the template
- To get to the User Account category, on the Manage Servers screen, click the
 category for the Private or Group Policy in the row of the desired server.
category for the Private or Group Policy in the row of the desired server. - Click New.
- Fill in the General tab – see next example:
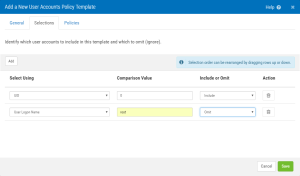
- Click on the Selections tab and click Add.
- Choose UID from the drop-down and specify 0 for the Comparison value.
- Click Add again and omit User Logon Name root from being examined (we know that root should have UID of 0).
- Click Save.
Or, go to Servers and Policies > [server name]. In the drop-down lists, select whether this should be a Private or Group Policy, then select User Accounts.
Run a compliance check
When you run a compliance check on this template any user account that has a UID of 0 – with the exception of root, will be identified as being out of compliance.
To run a compliance check, do one of the following:
- Click
 next to the template name (under the Action column).
next to the template name (under the Action column). - Check the box next to the template name and then click CheckIt.
- Go to Servers > CheckIt, choose the server.
NOTE: This runs a compliance check against all templates in the User account category.
- Create a cron job to run the compliance check. Go to Admin tasks > Manage Scheduled Jobs (creating scheduled jobs is discussed later).
If the template is out of compliance (indicated by a  in the Compliant column), click on the template name and then the Compliance tab to determine the accounts out of compliance. (In this case, the accounts with UID of 0.)
in the Compliant column), click on the template name and then the Compliance tab to determine the accounts out of compliance. (In this case, the accounts with UID of 0.)

 Previous
Previous