Testing a Wireless Environment
The use of 802.11 wireless networks (WiFi) is increasing throughout the enterprise. With WiFi, security professionals are presented with a new realm of challenges as attackers no longer need to be physically plugged in to access information systems. Core Impact provides several ways in which testers can evaluate the security of these wireless networks which serve as both keepers of and conduits to sensitive data.
Although the WiFi tests are not among Core Impact's Rapid Penetration Test (RPT), they are simple to launch and easy to integrate into one's penetration testing practice. The WiFi tests are executed from the Modules View so, if you are not already familiar with how to run modules directly, review the section Working With Modules. Additionally, see the section Wireless Vector Reporting for how to report on your wireless penetration test results.
When you discover wireless networks and devices, they will be represented in the Wireless folder of the Network tab of the Entity view as shown below.
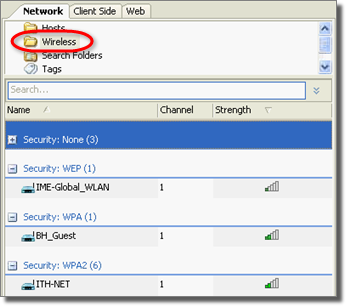
figure 15 - Wireless Entities
As mentioned, the WiFi testing capabilities in Core Impact are accessed directly through modules, but we will use the RPT model (Information Gathering, Attack & Penetration, Privilege Escalation, Clean Up, Report Generation) to organize and describe the available modules as well as to highlight any noteworthy parameters.
The below tests are specifically designed for use on WiFi networks. The modules are available by navigating to the Modules View and expanding the WiFi folder (ensure that the Network entity tab is active):
In order to create a Fake Access Point using Core Impact, you must use a Pineapple Mark VII (https://shop.hak5.org/products/wifi-pineapple) wireless network auditing tool.
The following sections will cover each phase of a WiFi test in greater detail.