Protocol: Download Action
(Requires FTC module) You can configure an Event Rule to copy or download from a specific location to a specified local folder using a particular protocol when an Event occurs. You must provide EFT with connection information (protocol and login details) and file information (source path and destination path). The Download Action is available with all Events except Site Stopped and Service Stopped.
-
When you add a Download file from host Action to a Rule, the Client FTP offload engine performs retries upon failures (network failures is the typical example) based upon the settings in the Advanced Options dialog box. Be aware that the Download file from host Action does the transfer, including all retries, before moving on to the next Action, such as an email notification. A long-running transfer that also retries numerous times with large delays will cause the Event Rule to take a long time to complete.
-
When setting up the File Download Action using variables, the remote connection test fails because variables appear undefined.
Refer to Connection Profiles for details of setting up a Connection Profile before defining the Action.
To set up EFT to download files
-
Follow the procedure in Creating Event Rules or select the Rule to which you want to add the Action.
-
In the Actions list, click Protocol: Download. The Rule parameters are added to the Rule in the Rule Builder.
-
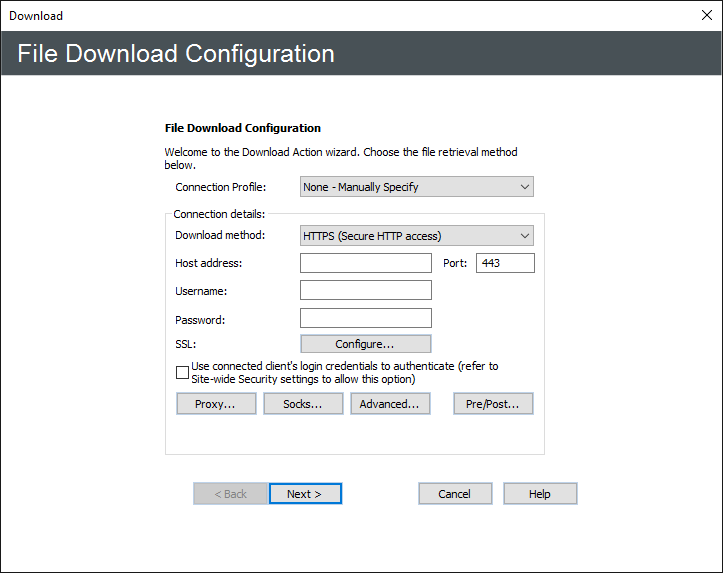
Click one of the undefined parameters where the parameters are listed in the Rule Builder. The File Download Configuration wizard appears.
-
In the Connection Profile box, specify a connection profile for this Event. If none is specified, you will need to configure the Connection details as described below.
-
Click the list to specify a Download method for the connection: Local (Local File or LAN), FTP (standard File Transfer Protocol), FTP SSL/TLS (AUTH TLS), FTP with SSL (Explicit encryption), FTP with SSL (Implicit encryption), SFTP using SSH2 (Secure Shell), HTTP (HyperText Transfer Protocol), HTTPS (Secure HTTP access).
- (Optional) If you selected Local (Local Files or LAN), provide the Windows account username and Password for connecting to remote shares (not local folders).
-
Think of Local Transfer as an operation (offload or download) with a remote server.
-
Think of "Optional credentials override") as "credentials to access remote server."
-
For download action, it is "credentials for source folder."
-
For copy/move (offload ), it is "credentials for destination folder."
-
"Credentials to access local folder" ("source" for offload and "dest" for download) is Event Rule execution context (EFT account, or Folder Monitor account for FM rules, or Connected Client account for client-originated rules on an AD site):
-
Download: local (EFT) <= remote ("override credentials")
-
TEST1: Offloads file from "local" Share A (access as EFT account, i.e., X) to "remote" folder B (access as Y) => Fails, as X has no permissions on A.
-
TEST2: Downloads file from "remote" Share A (access as Y) to "local" folder B (access as EFT account, i.e., X) => Succeeds, as Y has permissions on A and X has permissions on B.
-
If you chose anything but Local do the following; otherwise, skip to the Source File page step.
-
In the Host address box, type the IP or host address of the EFT to which you want to connect.
-
The Port number for the selected protocol changes automatically based on the offload method. Provide a different port number, if necessary.
-
In the Username and Password boxes, type the username and password used to authenticate.
-
-
Select the Use connected client's login credentials to authenticate check box if you want to use the local system account to authenticate. The availability of this check box is controlled by the Persist username and password credentials for use in Event Rule context variables check box on the Site's Security tab.
-
If you chose SFTP, provide the client SFTP certificate information.
- If you chose a protocol that uses SSL (FTPS or HTTPS), provide the client and remote server's SSL certificate information.
-
If you are connecting to a remote host through a SOCKS server, click SOCKS and provide the SOCKS connection information.
-
If you are connecting to a remote host through a proxy, click Proxy. Provide the proxy connection information.
-
To specify transfer options and time stamps, click Advanced. Specify the advanced transfer options, such as connection retry attempts and delay between retries.
-
To specify pre or post commands for connections to a mainframe computer, refer to Pre and Post Commands
-
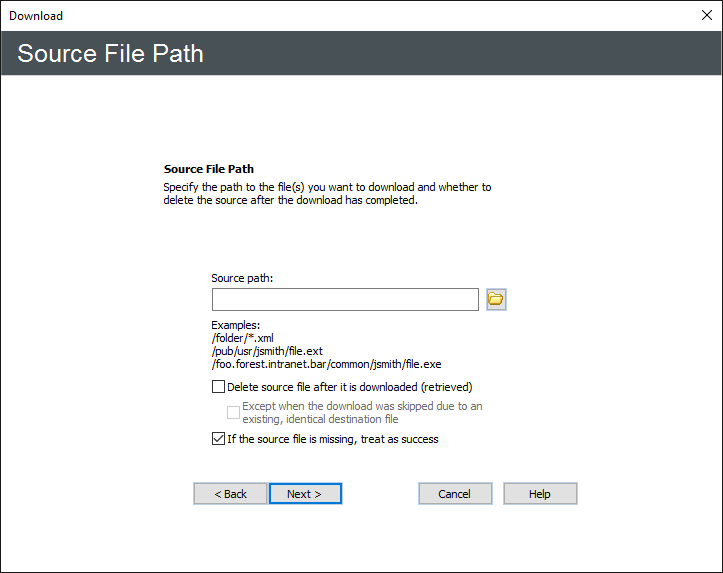
Click Next. The Source File Path page appears.
-
In the Source path box, provide the path to the file(s) that you want to download. For example, type:
-
Select the Delete source file after it is downloaded check box if you want to delete the file after it is retrieved. (If the file is marked read-only, it will not be deleted.)
-
Select the Except when ... check box if you do not want to delete the source file after it is downloaded if the download was skipped.
-
Select the If source file is missing, treat as success check box to treat remote file downloads as success, even if file is missing. (The client DLL in EFT doesn't have a mechanism for detecting if the file exists on the remote server or not.)
-
For LAN/local transfers only, select the If the source file is missing treat as success check box if you want the Action to be considered successful even if the source file is missing.
-
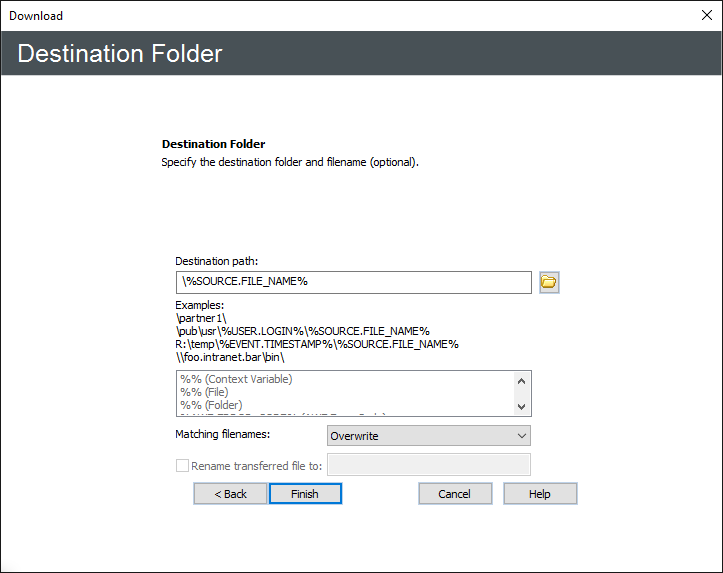
Click Next. The Destination File Folder page appears.
-
The optional folder synchronization feature can also synch the destination folder with the source folder (2-way synchronization).
-
In the Destination folder box, click the folder icon
 and
specify the location in which to save the downloaded file. You can
insert variables by double-clicking them in the box below the Destination folder box.
and
specify the location in which to save the downloaded file. You can
insert variables by double-clicking them in the box below the Destination folder box. -
In the Matching filenames box, specify whether to Overwrite, Skip, or Numerate files that exist with the same name. If Overwrite is selected, EFT performs a CRC match for the files.
-
If desired, select the Rename transferred file to check box, then specify a new name.
-
Click Finish, then click Apply to save the changes on EFT and/or add other Actions and Conditions to the Rule.
These credentials are used only if/when a resource cannot be accessed using the credentials under which the EFT service is running. The Optional credentials override feature allows you to specify an alternate set of logon credentials for accessing remote network shares to which the EFT service account may not have access (due to security constraints).
If alternate credentials are specified, EFT will use its current security token (associated with the “Log on as” account specified in the EFT service settings) for local folder access and then new security token (associated with the alternate logon credentials) for the remote source folder accessed over network connections (e.g. network shares).
/pub/usr/jsmith/file.txt or \\mydomain\common\jsmith\file.txt
If you type a path to a remote folder that does not exist, the Event Rule will fail.