![]()
This section describes configuring Mail Express for use with DMZ Gateway. For information about installing and configuring DMZ Gateway, please refer to the DMZ Gateway documentation.
|
This section describes configuring Mail Express for use with DMZ Gateway. For information about installing and configuring DMZ Gateway, please refer to the DMZ Gateway documentation. |
Mail Express Server can connect to a network protected by DMZ Gateway v3.0.1 and later. Using DMZ Gateway with the Mail Express Server allows administrators to limit access by allowing only outbound connections from the Mail Express Server via the firewall configuration. DMZ Gateway is designed to reside in the demilitarized zone and provide secure communication with the Mail Express Server behind intranet firewalls without requiring any inbound firewall holes between the internal network and the DMZ, and with no sensitive data stored in the DMZ, even temporarily. When configured to use DMZ Gateway, Mail Express functions normally, giving no indication to end users of the system that the additional piece has been added to the network.
By default, only the Pickup, Dropoff, and Reply portals are accessible via DMZ Gateway. The Administration portal, Internal portal, and Outlook Add-In web service interface (interfaces usually accessed from within the network) are not accessible via DMZ Gateway.
DMZ Gateway is a separate module from Mail Express Server and is installed and licensed separately. The connection between Mail Express and DMZ Gateway is configured in the Mail Express administration portal. You must enable an outbound port from Mail Express Server to DMZ Gateway over which Mail Express Server is to connect to DMZ Gateway. The default port is 44500. Mail Express only communicates over HTTPS, which uses port 443 by default.
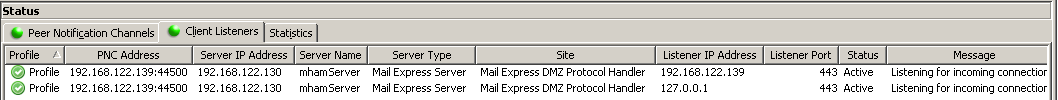
In the DMZ Gateway interface, the Mail Express Server is considered a "Server" and the Mail Express DMZ Protocol Handler is considered a "Site" (e.g., in the DMZ Gateway Status pane). In the DMZ Gateway version 3.1.0, when communicating with Mail Express Server, "Mail Express Server" appears in the Server Type column. In earlier releases of DMZ Gateway, “[Unknown]” appears in the Server Type column.
DMZ Gateway events are logged in the Mail Express Event log.
For details of installing and configuring DMZ Gateway, refer to the DMZ Gateway in-application help or online help.
Before you can use DMZ Gateway with Mail Express Server, you have to provide Mail Express with the DMZ Gateway connection information.
To configure the DMZ Gateway information
Launch the Mail Express Server administration interface. (e.g., click Start > Programs > Globalscape > Mail Express > Mail Express Admin or double-click the desktop shortcut).
Log in using the Mail Express Server administrator username and password that you specified during installation of the server.
In the navigation pane or on the Mail Express Status page, click DMZ Gateway. The DMZ Gateway Configuration page appears.
Select the Enable the DMZ Gateway as a proxy check box. The page expands to display more options.
Under Access Settings, specify which portals are to be accessed through the DMZ Gateway address, and whether LDAP authentication is to be used for portals accessed through DMZ Gateway.
In the SSL Certificate section, provide the SSL certificate information.
In the Require Client Certificate Validation box, specify whether validation is required.
In the Upload Certificate Authority certificate chain area, click Browse to find the signed certificate file (.crt).
In the Upload public certificate area, click Browse to find the public certificate.
In the Upload private key area, click Browse to find the key file for the certificate (.key).
If a password is required for this certificate, select the Private key is password protected check box, then provide the password in the Private key password and Confirm private key password boxes.
Under Portal Settings, in the DMZ Gateway address box, specify the hostname or IP address of the DMZ Gateway.
In the Server Port box, specify the port number used by DMZ Gateway (44500 by default).
In the Client HTTPS Port box, specify the port on which DMZ Gateway listens for incoming client connections. In the case of Mail Express, client connections will typically include external recipients picking up files via the Pick-Up portal and external users dripping off files via the Drop-Off portal.
While the DMZ Gateway supports use of client ports other than port 443, it is highly recommended to use the default HTTPS port of 443 as this is the industry standard for HTTPS communications. When using the standard port, users will not have to specify a port value in the browser's URL if they are manually typing the URL to connect to a portal such as the Drop-Off portal.
Using a non-standard client HTTPS listener port will require either adding the port to the General Configuration Hostname so that the port is included on links generated by the Mail Express system, or the networking infrastructure must be configured using port-forwarding to redirect external HTTPS traffic to the configured Client HTTPS port on the DMZ Gateway computer.
Click Save to save the changes or click Restore to return to the previous settings.
If the connection to DMZ Gateway was lost (e.g., due to network errors), you can click Reconnect or wait 30 seconds for the Mail Express server to automatically try to reconnect. If the connection fails, the reason appears in the Extended Status Message box.
If EFT is installed, on the EFT Configuration page, you can select the Auto sync EFT configuration to synchronize Mail Express settings automatically with EFT configuration. When Auto sync is specified, if you change the port or IP address in EFT that DMZ Gateway uses, it will automatically update in Mail Express. If you would rather view and enable or disable individual settings, you can do so by clicking Sync on the DMZ Gateway Configuration page.
To specify which DMZ Gateway settings to sync
On the DMZ Gateway Configuration page, click Sync. The selection page appears.
Select the check box of the items you want to sync; clear the check box of items that you do not want to sync.
Click Sync. The settings in Mail Express are synchronized with the settings in EFT. Configuration changes that occur during a sync (auto or manual) are audited in Mail Express's Configuration History report.
For security, communications routed through the DMZ Gateway are denied access to the Administration portal, Internal User portal, and Outlook Add-In web service interfaces by default. Typically, communications to these portals should only come from the internal corporate networks. This functionality allows limiting access to portals similar to the functionality provided by a web application firewall.
Additionally, authentication that takes place through the DMZ Gateway will not authenticate against Active Directory/LDAP, if applicable. This provides an additional layer of security against brute-force attacks on Active Directory accounts.
To modify these settings
In a text editor, open the file <Installation Directory>\webapps\ROOT\WEB-INF\classes\META-INF\staticConfig.xml.
Modify one or more of the following settings:
configurationManager.enableLDAPViaDMZGateway - Sets whether authentication should be performed against LDAP for communications that have been proxied through the DMZ Gateway. Default is false.
configurationManager.enableAdminPagesViaDMZGateway - Sets whether Administration portal pages should render for communications that have been proxied through the DMZ Gateway. Default is false.
configurationManager.enableDropoffPagesViaDMZGateway - Sets whether Drop-Off portal pages should render for communications that have been proxied through the DMZ Gateway. Default is true.
configurationManager.enableInternalPagesViaDMZGateway - Sets whether Internal portal pages should render for communications that have been proxied through the DMZ Gateway. Default is false.
configurationManager.enablePickupPagesViaDMZGateway - Sets whether Pickup portal pages should render for communications that have been proxied through the DMZ Gateway. Default is true
configurationManager.enableClientServiceViaDMZGateway - Sets whether the Outlook Add-In web service interface should be enabled for communications that have been proxied through the DMZ Gateway. Default is false
configurationManager.enableReplyPagesViaDMZGateway - Sets whether the Reply portal pages should render for communications that have been proxied through the DMZ Gateway. Default is true
configurationManager.enableAccountActivationPagesViaDMZGateway - Sets whether account activation portal pages should render for communications that have been proxied through the DMZ Gateway. Default is true
Save the changes to the file.
Restart the Mail Express Server Windows service.