![]()
To use NT/AD authentication, users need "Log On Locally" access to the computer on which GlobalSCAPE EFT Server is installed, no matter what kind of computer it is or the role it plays on the network, including a domain controller.
When Active Directory (AD) authentication is chosen, EFT Server impersonates the user, passing the user’s credentials to the AD domain controller for authentication. When the user attempts an action, they are permitted or denied by the NTFS permissions associated with that file or folder as they apply to that user. EFT Server attempts to "synchronize" the NTFS permissions information on every folder and file, physical or virtual, throughout the entire VFS, and then internally imposes permissions based on its last scan of the file system.
|
|
To use NT/AD authentication, users need "Log On Locally" access to the computer on which GlobalSCAPE EFT Server is installed, no matter what kind of computer it is or the role it plays on the network, including a domain controller. |
EFT Server lists and authenticates all AD login accounts, even when multiple accounts have the same display name. EFT Server uses the proper login credentials (SAMAccountName, (The logon name used to support clients and servers running older versions of the operating system, such as Windows NT 4.0, Windows 95, Windows 98, and LAN Manager. This attribute must be less than 20 characters.) UPN, GUID, etc.) used by the AD controller to uniquely identify accounts. EFT Server uses the SAM account name to index the list of user accounts, and only one of the accounts is displayed in the list of users and only one is used for authentication if the display names are identical. In addition, EFT Server recognizes that UserName1 and DomainName\UserName1 are the same login account and does not create a second account. EFT Server allows the selection of the login name type for each Site that uses AD.
EFT Server supports the listing of user accounts and login authentication for accounts that reside in remote AD domain groups referenced by an AD universal group. EFT Server only supports accounts that reside in groups that are from the same domain as the universal group. EFT Server supports traversal of the remote groups referenced by a universal group. The recursive traversal of groups and subgroups that exist in EFT Server continue to be supported and are unaffected by the ability to support users in remote groups that are referenced by a local universal group.
EFT Server can create Sites (In EFT Administrator, a Site is similar to a virtual FTP server bound to one or more IP addresses.) using the NT user authentication database, allowing users to connect to the Site with their NT user name and password. Permissions are assigned to users from the NT user database on the domain of the system that is running EFT Server. EFT Server queries the Primary Domain Controller (PDC) for your domain and adds all domain users.
|
|
EFT Server uses "impersonation" when logging in to an AD/NTLM Site and "piggy backs" on top of the operating system permissions/settings for all folder/file access. If you are using Access Based Enumeration (ABE) Access Based Enumeration; on Windows 2003 Server, ABE makes visible only those files or folders that the user has the rights to access. on the Windows Server and have configured EFT Server to use Windows Authentication, point the root folder or VFS path to the UNC Share that has ABE turned on. (Note that ABE operates on network shares, not on NTFS.) |
Users are listed as soon as you open the Site you created using NT Authentication. You cannot add or change users from EFT Server, but you can change their permissions, settings, and status on EFT Server.
|
|
NT Authentication transmits passwords over the network without data encryption. To avoid exposing your passwords to possible theft, use SSL connections with NT Authentication. |
To create an NT-authenticated Site
The Site Setup wizard appears after you complete the Server Setup wizard; otherwise, in EFT Administrator, click Configuration > Create New Site, or right-click anywhere in the Server's tree, then click Create New Site.
Do one of the following:
To create a HS-PCI-enabled Site, refer to Creating an HS-PCI-Enabled Site
Click Use standard security settings.
Click Next. The Site Setup wizard Welcome page appears.
In the Site Name box, type a name a distinguishing name for the Site.
In the Listening IP box, select a specific IP address or keep the default of All Incoming.
Click Next. The Site Root Folder page appears.
In the Site root box, click Browse to specify the root folder, or keep the default.
In the Additional options area, select the check boxes as needed:
Select the Create UNIX-style subfolders check box to create Usr, Pub, Bin, and Incoming folders with appropriate permissions under the root folder. This is only necessary if you are trying to mimic a typical default *nix EFT Server setup.
Select the Automatically assign home folders to newly created users to automatically create a user folder under \Site Root\Usr\ when a new user is added.
|
|
Both check boxes are selected by default. You need to specify home folders for users even if you are using Active Directory (AD) authentication. If the Automatically assign home folders check box is selected, EFT Server creates virtual folders under the Site's physical root folder that points to the users' home folders assigned in AD. |
Click Next. The User Authentication page appears.
In the Authentication type list, click Windows Active Directory Authentication.
Click Next. The NT Authentication page appears.
In the Authentication type area, click Active Directory or NTLM to match the authentication method used on EFT Server's domain.
In the Domain Context area, do one of the following:
Click Use default if you want to use the authentication database from the computer's current domain.
Click Custom, then in the Context box, provide the domain name that contains the authentication database.
In the Allow access to the following group area, do one of the following:
To allow access to every user in the domain's database, click Everyone.
To allow access to only a specific AD Group, click Custom, then in the Group box, type the group name for users that will have access to EFT Server.
To verify your settings, click Test.
In the Use this user attribute as the logon name box, click the down arrow to specify the attribute to use (NT 4 Account Name, Display Name, User Principal Name, Common Name).
In the User list refresh interval box, click the down arrow to select how often you want EFT Server to check the authentication database for new users (server specified, never, or from 5 minutes to 1 day).
Click Next. The Perimeter Security page appears.
Specify whether to connect the Site to EFT Server's DMZ Gateway.
If you choose to connect to DMZ Gateway, specify its IP address and port, then click Test Connection. If the DMZ Gateway is properly configured, the Test is successful. If the test is not successful, click and I'm not using the DMZ Gateway configure it later.
If you have not yet installed or configured DMZ Gateway, click I'm not using the DMZ Gateway - or I'll configure it later.
Click Next. The Connection Protocols page appears.
Select one or more check boxes for the protocol(s) and port numbers that this Site will use to connect to EFT Server.
Click SSL options to define the allowed SSL versions and ciphers or skip this step and leave the defaults.
Click SSL certs to specify the SSL certificate
to use for this Site. The SSL Certificate
Options page appears.
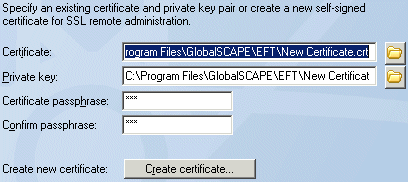
To create a certificate, click Create certificate and follow the prompts in the wizard. (Refer to Creating Certificates for details, if necessary.)
To use an existing certificate:
In the Certificate box, type the path to the .crt file or click the open icon to find and select it.
In the Private key box, type the path to the .key file or click the open icon to find and select it.
In the Certificate passphrase and Confirm passphrase boxes, type and confirm the passphrase for the certificate pair.
Click Next to return to the Protocols page.
|
|
If you do not enable SSL, you will not be able to connect to EFT Server from a remote EFT Administrator. See SSL Certificate-Based Login, Creating Certificates, Importing a Certificate into the Trusted Certificate Database, and Importing Certificates from Microsoft IIS 5 for information regarding certificates. If you are using Secure Ad Hoc Transfer, you need to configure remote access to EFT Server. |
If you choose SFTP, the SFTP options are configured automatically. Optionally, click SFTP options and SFTP keys to configure a different SFTP key pair, encryption algorithms, and MAC algorithms. (All algorithms are selected by default.)
If you choose AS2 over HTTP/S, click Configure to specify your AS2 identifier and certificate information. The certificate that you specified in step 10 is specified by default. You can keep this default, click the open icons to specify a different certificate pair, or click Create certificate to create a new certificate pair, then click OK.
Click Next. The Site Configuration Completed page appears.
You are offered the option of continuing to the User Creation wizard or quitting the Site Setup wizard. Click an option, then click Finish.
If you chose Run New User Creation wizard, the User Creation wizard Welcome page appears.
Remember to configure permissions to virtual folders in the Virtual File System.
You can run the Site Setup wizard again at any time to create additional Sites. You can view and modify Site configuration in EFT Administrator.