Windows Registry Settings
EFT Server stores its configuration information in the Windows Registry,
which contains profiles for each user of the computer and information
about system hardware, installed programs, and property settings. EFT
Server modifies the system registry as needed, and continually references
this information during operation.
To add a key to the registry, you can either edit it directly or create
and execute a .reg file. When you add or edit these registry keys, you
will need to restart EFT Server.
|

|
These options are for advanced users only. Incorrectly
editing the registry can severely damage your system. You
should always back up (export a copy of) the registry before you make
any changes to it.
Certain keys below should be created in the EFT Server
3.0 folder, and others in the EFT Server 4.0 folder. Do
NOT change the path to match your version of EFT Server. |
The registry keys described below are available in EFT Server for advanced
system administration.
To backup the registry
Click Start >
Run. The Run
dialog box appears.
In the Open box,
type regedit,
then press ENTER. The Registry Editor
appears.
Do one of the following:
To backup the
entire registry, click My Computer.
To backup a
specific group of keys or a specific key, click the folder or key.
On the main menu, click File
> Export. The Export Registry File dialog box appears.
Specify a name and location for the file, then click
Save. The export process begins.
If you are exporting the entire registry,
it can take a few minutes, and the file size can be up to 100 MB or more.
If you are exporting just one key, the file size is approximately 1 KB.
After you edit the registry, if you are experiencing
problems caused by editing the registry, you can import the backed up
file:
On the main
menu, click File > Import.
The Import Registry File dialog
box appears.
Click the
.reg file to import, then click
Open. The import process begins.
If you are importing the entire registry, it can take a few minutes.
To create a .reg file
In a text editor, such as Notepad, type or paste the
following text on the first line:
Windows Registry Editor Version 5.00
On the second line, type or paste the key path. For
example, type:
[HKEY_LOCAL_MACHINE\SOFTWARE\GlobalSCAPE Inc.\EFT Server
4.0\EventRules]
(include brackets)
On the third line, type or paste the name of the key
and the value (DWORD) for the key. For example, type:
"FolderMonitorWorkerThreadCount"=dword:00000100
(include quotation marks)
Close the file and save it with a .reg extension.
For example, type:
threadcount.reg
Double-click the file and follow the prompts to install
the key into the registry. If you receive an error, open the file to verify
the information was typed correctly. The .reg file
can be transported to and used on other computers.
To create the key manually
Click Start >
Run. The Run dialog
box appears.
In the Open box,
type regedit,
then press ENTER. The Registry Editor
appears.
Expand the My Computer node, the HKEY_LOCAL_MACHINE
node, and the SOFTWARE node to find the GlobalSCAPE nodes.
Click the applicable GlobalSCAPE node (as described
below), then right-click it, point to New,
then click Key. This makes a new
folder under the GlobalSCAPE node.
Type a name for the key based on the instructions below,
then press ENTER.
Right-click the key, point to New,
then click DWORD Value.
Type a name for the DWORD value based on the instructions
below, then press ENTER.
Double-click the DWORD. The Edit
DWORD Value dialog box appears.
In the Value data box,
type an integer (based on the instructions below), then click OK.
Close the registry, then restart the Server service.
|

|
Some of the keys below should be created in the EFT Server
3.0 folder, and some should be created in the EFT Server 4.0 folder. Do NOT change the path to match your version
of EFT Server. |
Specify Location of FTP.CFG
In EFT Server 4.0.8 and later, you can create
a registry key to override the location of the FTP.CFG file. When this
key is present, the FTP.CFG is loaded from the specified path instead
of the default, which is the folder hosting the executable. This feature
was added to help with multiple nodes using the same configuration, such
as active/passive configurations.
HKEY_LOCAL_MACHINE\SOFTWARE\GlobalSCAPE Inc.\EFT Server
4.0\Config
"Path=<path_to_config_file>"
For example, If you want EFT Server to use the CFG file at G:\Configs\EFT\FTP.cfg,
you would create the following registry value:
HKEY_LOCAL_MACHINE\SOFTWARE\GlobalSCAPE
Inc.\EFT Server 4.0\Config\Path="G:\Configs\EFT\"
Include the trailing backslash. UNC paths can be used as well. The Server
service must be run under an account that has access (NTFS) to the specified
resource. (For instance, if it is logging in as LocalSystem and the CFG
file is not saved to the shared drive.)
Kill EAS Service on Startup
If this registry key is present and set to
"1", EFT Server will find and kill any EASServer.exe processes.
HKEY_LOCAL_MACHINE\Software\GlobalSCAPE Inc.\EFT Server
4.0\
"KillEASServersAtStartup"=dword:00000001
Changing the Number
of Concurrent Threads Used by Event Rules
The Event Rule Monitor Folder process is limited to 3 concurrent threads
by default. This means that if you have 5 Folder Monitor Event Rules monitoring
the same folder, and a file is added to the monitored folder, only 3 of
the 5 Rules will fire, as determined by the operating system. The 4th
and then 5th Rule execute only when one or more of the first three threads
are done firing and executing any actions. If you have, for example, 100
concurrent Monitor Folder Event Rules, they are not all triggered simultaneously.
To override the default, create the following key:
"HKEY_LOCAL_MACHINE\SOFTWARE\GlobalSCAPE Inc.\EFT
Server 4.0\EventRules\FolderMonitorWorkerThreadCount"
(DWORD: the number of allowed concurrent
threads)
Enable Alternative
Permission Logic
This registry key determines whether EFT Server checks for the "Delete"
permission when a client uploads a file.
If this setting is not present and/or set to zero, when
a connecting client uploads a file, EFT Server checks only for Upload
permission. If a file already exists with the same name, it will be overwritten.
If this registry setting is present and non-zero, then
EFT Server determines if an upload will delete (overwrite) an existing
file. If a file already exists, EFT Server does an additional check for
Delete permission.
"HKEY_LOCAL_MACHINE\SOFTWARE\GlobalSCAPE Inc.\EFT
Server 4.0\Config\UplReqDel"
(DWORD: if non-zero value, EFT Server checks if client
has Delete permission.)
Web Transfer Client Registry
Overrides
You can override the hard-coded location of the Web Transfer Client
files by settings some registry values to indicate the new location of
the files you would like to use. The registry key indicates the specific
file used by the Web Transfer Client, and the value of the key indicates
the full file path to use for the file.
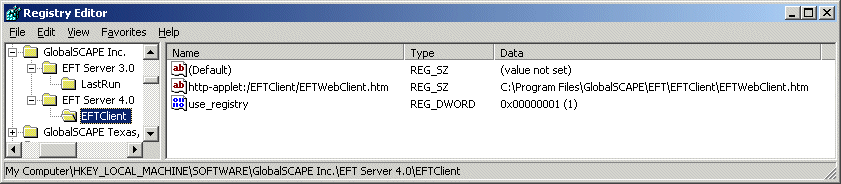
To use this key, set use_registry dword to 1 (same
path).
[HKEY_LOCAL_MACHINE\SOFTWARE\GlobalSCAPE
Inc.\EFT Server 4.0\EFTClient\]
http-applet:/eftclient/eftwebclient.htm
http-applet:/eftclient/EFTAppletFunctions.js
http-applet:/eftclient/eftwebclientlogic.js
http-applet:/eftclient/EFTStyles.css
http-applet:/eftclient/eft.jar
http-applet:/eftclient/chttpclient.jar
http-applet:/eftclient/httpimpl.jar
http-applet:/eftclient/jclientupload.jar
http-applet:/eftclient/clogging.jar
http-applet:/eftclient/weakssl.jar
You can add each of the keys
you need to a .reg file in
the following format:
|
Windows Registry
Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\GlobalSCAPE
Inc.\EFT Server 4.0\EFTClient]
"use_registry"=dword:00000001
"http-applet:/EFTClient/EFTWebClient.htm"="C:\\Program
Files\\GlobalSCAPE\\EFT\\EFTClient\\EFTWebClient.htm"
|
Less commonly used Web Transfer
Client Registry Overrides:
http-applet:/eftclient
http-applet:/favicon.ico
http-applet:/eftclient/META-INF/services/org.apache.commons.logging.LogFactory
http-applet:/org/apache/log4j/Logger.class
http-applet:/javazoom/transfer/client/util/resources.class
http-applet:/javazoom/transfer/client/util/resources_en.class
http-applet:/javazoom/transfer/client/util/resources_en_US.class
http-applet:/javazoom/transfer/client/util/resources_en_US.properties
http-applet:/eftclient/commons-logging.properties
http-applet:/javazoom/transfer/client/util
http-applet:/org/apache
Other Registry Overrides:
http-applet:/ManageAccount
EFT Server Transfer Engine
Stub
Windows Registry Editor Version
5.00
[HKEY_LOCAL_MACHINE\Software\GlobalSCAPE Inc.\TED 6\Settings\Connection]
[HKEY_LOCAL_MACHINE\Software\GlobalSCAPE Inc.\TED 6\Settings\Transfer]
"PASVMode"=dword:00000001
Setting 2 is PASV mode; setting 0 is PORT mode
Reverse Banned File Logic
On the Advanced tab for a Site,
you can block
the upload or download of certain file types. The key below reverses that
"banned file logic" from the current "By default allow
all files except those below:" to "By default exclude all files
except those below:” That is, a REVERSAL of the current logic, The reversed
logic filters out ALL by default, and only allows in those that the administrator
specifies. (For example, if you want to allow only .txt files.)
To activate this feature, create the following key:
"HKEY_LOCAL_MACHINE\Software\GlobalSCAPE Inc.\EFT
Server 3.0\RestrictionByFileNameOnUpload"
(DWORD; non-zero means reverse the logic for banned files [exclude all
except those listed])
HTTP->HTTPS
Redirection
In EFT Server 5.1 and later, if you have installed the HS-PCI module,
you can redirect HTTP connections to HTTPS on the Connection
Options tab of the Site. The HTTP engine listens to a specified
port (default 80) even when OFF; all traffic is redirected to the HTTPS
port on the same host (using HTTP header), by responding with a redirect.
To activate this feature prior to version 5.1 or if your
HS-PCI module has expired, create the following key:
"HKEY_LOCAL_MACHINE\Software\GlobalSCAPE Inc.\EFT
Server 3.0\RedirectHTTPtoHTTPS"
(DWORD; non-zero means all traffic coming to HTTP port will be redirected
to HTTPS port using HTTP protocol (header redirection).
|

|
The HTTP port will be LISTENING even if the check box
is OFF for that protocol, including through DMZ
Gateway.
The connecting client might receive the 302 status/error
code, which means the connection was moved. |
Upload Throttling
The keys below can be used to prevent a connected client from uploading
more than <n> files in <t> seconds.
To activate this feature, create the following keys:
"HKEY_LOCAL_MACHINE\Software\GlobalSCAPE Inc.\EFT
Server 4.0\Config\UploadsPerClient"
(DWORD; this is the count
of uploads allowed in the period)
"HKEY_LOCAL_MACHINE\Software\GlobalSCAPE Inc.\EFT
Server 4.0\Config\UploadsPerClientInterval"
(DWORD; this is the interval
period, in seconds)
ODBC Auth Manager
This key only applies to external ODBC user authentication databases
to allow for the "Settings Level" column in the database to
specify into which settings level a user is placed for new user creation
and any synchronization to move a User Setting Level (and home folder)
when changed in the database. Refer to Creating
Tables for you ODBC Data Source for details of the database tables.
A SQL
script is provided that will create the necessary tables.
To activate this feature, create the following key:
"HKEY_LOCAL_MACHINE\Software\GlobalSCAPE Inc.\EFT
Server 3.0\EnableODBCSettingsLevelField"
(DWORD; non-zero to enable
the feature)
Maintain Password History
for "Change Password" Validation
In EFT Server 5.1 and later, you can set the password
history in EFT Administrator. Remembering the last <n>
passwords is also configurable in the registry. This registry setting
is available only with "GlobalSCAPE Authentication" and the
password type must be "Standard" (Regular).
To activate this feature in versions prior to 5.1, create
the following key:
"HKEY_LOCAL_MACHINE\Software\GlobalSCAPE Inc.\EFT
Server 3.0\PasswordHistoryLimit"
(DWORD; 0 means no history)
Legacy SMTP Send Behavior
This key is used for communicating with legacy SMTP servers that do
not support RFC
1652 or if having trouble sending messages through your existing
SMTP server.
"HKEY_LOCAL_MACHINE\Software\GlobalSCAPE Inc.\EFT
Server 4.0\LegacySMTPSendBehavior"
(DWORD; non-zero to enable
the feature)
HTTP Engine Use Server
Time Zone
In EFT Server version 5 and later, you can create/edit this registry
key to alter the behavior of the HTTP/S engine's directory listing format.
By default, files and folders are displayed using UTC; however, if this
registry value is present and non-zero, we use the Server's time zone
for file/folder listings in the HTTP/S engine.
0 - use UTC file times
!0 - use Server time zone for file times
HKEY_LOCAL_MACHINE\Software\GlobalSCAPE
Inc.\EFT Server 4.0\
"UseServerTimeZone"=dword:00000001
Folder Monitor Change
Filter Override
In EFT Server version 5.1.1 and later, you can create/edit a registry
key to set the "dwFilter" parameter that is passed into the
function "ReadDirectoryChangesW()", which is the core of the
Folder Monitor feature.
HKEY_LOCAL_MACHINE\Software\GlobalSCAPE
Inc.\EFT Server 4.0\EventRules
"FolderMonitorFilterValue"=dword:0000007D
The default value is:
FILE_NOTIFY_CHANGE_FILE_NAME | FILE_NOTIFY_CHANGE_ATTRIBUTES
| FILE_NOTIFY_CHANGE_SIZE | FILE_NOTIFY_CHANGE_CREATION | FILE_NOTIFY_CHANGE_LAST_WRITE
| FILE_NOTIFY_CHANGE_LAST_ACCESS
(This is a value of 0x7D)
This override is used to "quiet" folder monitor event dispatching;
for example, if only looking for NEW files added to the folder, then exclude
the "FILE_NOTIFY_CHANGE_FILE_NAME | FILE_NOTIFY_CHANGE_ATTRIBUTES
| FILE_NOTIFY_CHANGE_LAST_ACCESS" set.
Redirect Custom Command
Output to Connected FTP Clients
In EFT Server version 5.1.1 and later, you can create/edit a registry
location to cause the output of an Event Rule-executed custom command
(when "redirect output to client" is on) to be sent back over
the FTP command channel. This option is disabled by default (which is
legacy behavior), but setting this DWORD registry value to a non-zero
integer will result in this behavior. The Event Rule must be executed
SYNCHRONOUSLY for the output to be redirected to the client, so you should
ensure at least one IF FAILED Action is defined to force synchronous operation.
HKEY_LOCAL_MACHINE\Software\GlobalSCAPE
Inc.\EFT Server 3.0\
"FileUploadEventResult"=dword:00000001
Disable COMB Command
In EFT Server 5.1.1 and later, to avoid problems with multipart uploads
causing multiple file upload events, you can create/edit a registry location
to disable the COMB command on the Server. Restricting transfers to one-part
uploads will result in slower transfers, but will greatly reduce headaches
when you want to process uploaded files, because a file upload success
is the entire file. This option is disabled by default (legacy behavior),
but setting this DWORD registry value to a non-zero integer causes COMB
to be disallowed and not shown in the response to FEAT.
HKEY_LOCAL_MACHINE\Software\GlobalSCAPE
Inc.\EFT Server 3.0\
"DisableCOMBCommand"=dword:00000001
ClientFTP.DLL Enable Logging
Override
After a transfer is complete, EFT Server will remove log files. Starting
with EFT5.1, you can create/edit a registry location to cause the ClientFTP.DLL
engine to retain the client log files.
To activate this feature, create the following key:
"HKEY_LOCAL_MACHINE\Software\GlobalSCAPE
Inc.\TED 6\EnableLogging"
(DWORD:00000001)
Set the DWORD value to "1" to retain log files. The log files
appear in the same LOGS folder that the "cl" log files appear,
in the file name format of "[07.11.30_12.11]-#000004.log".
Other values under the Settings\LogWindows
key may need to be tweaked to ensure that logs are enabled and
not being deleted.
Most importantly, the following values need to be set
to 0 to prevent logs from being automatically deleted:
"DeleteSessionLogFiles" (one log per FTP session)
"DeleteItemLogFiles" (one log per FTP transfer)
"DeleteLogsAfterCloseTE" (deletes logs while
the client is unloaded)
"CloseFinishedItemLogs" (deletes logs for
successfully completed transfers)
You might also want to edit the following settings:
Disable the "DeleteOldLogs" setting or tweak
the "QuantityUnitForDeleteLogs" and "UnitForDeleteLogs"
settings, which affect how often old logs are deleted.
Ensure that the "EnableXferLog", "EnableMDILog",
and "EnableVFSLog" settings are set to 1 so that each of these
log types are created - these settings have more to do with the different
ways that CuteFTP can display logs than with the operation of the FTP
client, but leaving all of them enabled is probably the safest setting.
Turn on timestamps by setting "ShowLogTimeStamps"
to 1
Turn on raw directory listings by setting "TraceLIST"
to 1. (You can actually turn on additional functionality of "TraceLIST"
by setting it to 3 or 19 (adding a 2 bit and a 16 bit).
The settings below illustrate possible settings to enable logging, timestamps,
and raw directory listings.
HKEY_LOCAL_MACHINE\SOFTWARE\GlobalSCAPE
Inc.\TED 6\Settings\LogWindow
"DeleteSessionLogFiles"=dword:00000000
"DeleteItemLogFiles"=dword:00000000
"DeleteLogsAfterCloseTE"=dword:00000000
"CloseFinishedItemLog"=dword:00000000
"DeleteOldLogs"=dword:00000001
"QuantityUnitForDeleteLogs"=dword:00000003
"UnitForDeleteLogs"=dword:00000002
"EnableXferLog"=dword:00000001
"EnableMDILog"=dword:00000001
"EnableVFSLog"=dword:00000001
"ShowLogTimeStamps"=dword:00000001
"TraceLIST"=dword:00000001
Ignore Active Directory
Home Directories
(This feature was added in version EFT 5.1.6 and is not backwards compatible.)
This registry key is used to allow EFT Server to ignore Active Directory
(AD) home directories; that is, you do not want EFT Server to create virtual
directories that point to the AD home directories.
Using this key, if you set the IgnoreADHomeDirs
registry DWORD value to 1, when AD users log in to the Server,
rather than the Server creating a virtual folder that links to the user's
AD-defined folder, a folder is created under the Server root directory
using the user's login name (assuming you have selected the Automatically
create a home folder for newly added users check box when you created
the Site). Refer to Creating
a Site that Uses NT Authentication for details, if necessary.
|

|
This value only affects a new Site. Before creating the
AD Site, set the registry DWORD value, then restart the EFT Server service.
You must specify an AD Group when you create the Site. If the Site is
already created, you can specify the Group in the Authentication
Options dialog box. |
To activate this feature,
create the following key:
"HKEY_LOCAL_MACHINE\Software\GlobalSCAPE
Inc.\EFT Server 3.0\IgnoreADHomeDirs"
(DWORD; 1 to enable, 0 (default) to disable)
More information:
Suppose you want to create home folders that
follow a specific sequence other than the user's login name, such as user
first name underscore last name, e.g. John_Smith. You would first set
the IgnoreADHomeDirs
registry value (so that the virtual folder pointers are not created),
then after creating a Site and pulling in your AD users, you could use
EFT Server's COM API to quickly scan and assign each user to a home folder
using the naming convention/pattern desired. Of course, you would want
to automate the script and run it regularly to query for newly added users
that have not yet been assigned a home folder; otherwise, when they log
in, they will be assigned the default folder based on their login name.
If the Automatically create a home folder
for newly added users check box is not selected, and a user attempts
to login before you have assigned them a folder (either through COM or
manually), the user will not be able to list or see any directories (sort
of in limbo). So regularly running the script (or ensuring you manually
create the folder every time a user is added) is critical.
Enable Oracle
(EFT Server 5.1.7 and later) This key only
applies if you are using an Oracle auditlogger.dll provided by GlobalSCAPE.
With this key enabled, if the Server uses an Oracle database, you can
upgrade to future releases by installing your custom auditlogger.dll in
the Server installation directory.
To activate this feature, create the following key:
"HKEY_LOCAL_MACHINE\SOFTWARE\GlobalSCAPE Inc.\EFT
Server 3.0\DBType
(DWORD;
if the key does not exist or is
0 = MSSQL; 1 = Oracle
Buffered CFG
Writes
(In EFT Server 5.1.7 and later) The writing
of the configuration (cfg) file to EFT Server occurs 1 byte at a time.
This key enables the Server to write the file in "chunks" instead
of 1 byte at a time. If you are experiencing long delays when applying
changes to the Server, try enabling this key to improve response time.
To activate this feature, create the following key:
"HKEY_LOCAL_MACHINE\ SOFTWARE\GlobalSCAPE Inc.\EFT
Server 4.0\UseBufferedArchiveWriter"
(DWORD; 1 to enable, 0 or does not exist
(default) to disable)
Sending EFT Server Logs to the Windows Application
Event Log
(In EFT Server 5.2.6 and later; This is not
recommended, but was a special request from a customer.) This registry
setting sends EFT Server's log
to the Windows Application Event Log. (As of v5.2.11,
this key applies to both the .ex
and the .cl logs.)
To activate this feature, create the following key:
"HKEY_LOCAL_MACHINE\SOFTWARE\GlobalSCAPE
Inc.\CuteLogger
"LogToWindowsEventViewer"=dword:00000001"
(DWORD; 1 to enable, 0 or does not exist
(default) to disable)
Pass the Client's IP Address to the Authentication
Request
(In EFT Server 5.2.6 and later; This is not
recommended, but was a special request from a customer with a unique configuration.
This is not a standard part of the LDAP protocol.) With this registry
setting, EFT Server alters the password that is sent to LDAP (during the
BIND request) to take on the form <client IP>@@<password>.
To activate this feature, create the following key:
"HKEY_LOCAL_MACHINE\SOFTWARE\GlobalSCAPE
Inc.\EFT Server 4.0
"PasswordContainsClientIP"=dword:00000001"
(DWORD; 1 to enable, 0 or does not exist
(default) to disable)
Override Outbound on Listen IP
In EFT Server 5.2.11 and earlier, if an outbound
event was scheduled, EFT Server would use the first IP address in the
system's IP address list rather than the listening IP address for the
site. This behavior was changed in EFT Server 5.2.12 so that EFT Server
now uses the listening IP address. In recognition that this could adversely
affect some of our customers, we added a registry setting to revert to
the old behavior.
To return to the legacy behavior, create the following
key:
"HKEY_LOCAL_MACHINE\SOFTWARE\GlobalSCAPE Inc.\EFT
Server 4.0"
"LegacyListenIP"=dword:00000001
(DWORD; 1 to enable, 0 or does not exist
(default) to disable)
Related
Topics
System Requirements for EFT Server
Best Practices for Configuration and Validation
EFT Server and Microsoft Clustering Services
Upgrading EFT Server
Installing EFT Server and Administrator
Activating
the Software
Setting Windows System Services
Running EFT Server and Microsoft IIS on
the Same Computer
EFT Server in the Windows Event Viewer
Registrations, Licenses, End-User Agreement
![]()
