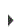More on Access Control Rules - green screen
The power of Exit Point Manager resides in its ability to control network access to IBM i network servers and server functions according to the rules you specify.
As discussed in Getting Started with Exit Point Manager, you can set rules for a User (user profile), Group profile, or Supplemental Group profile. For example, you can create a rule by user ID that directs the FTP server to reject any upload attempt from users who are members of a particular group profile. For more information on user rules, see User Rules.
Another method of defining an access rule is by location. A location is Exit Point Manager's definition of the origin of an access request. A location can be a specific IP, group IP, generic IP, range of IP addresses, or SNA device. (For example, a group of IP addresses may correspond to a corporate office's physical location, e.g. *DENVER). Location security rules allow you to grant access to, and define the authorities for, all approved dial-in and Internet origins, while restricting access to unapproved origins according to the rules you define. For example, you can create a location rule to direct the IBM i FTP server to reject any FTP request coming from outside your local network. See Location Rules.
Exit Point Manager also lets you set object rules that are configured at the object level, for a specific user or location, for a specific object, and for a specific type of access. Creating an object rule allows you to, for example, specify who can access your IBM i payroll database. See Object Rules.
Authorities
Access Control Rules establish the action to be taken when a particular server or server function is accessed. You can specify the following actions:
- *OS400 - Allow the request using the user’s normal IBM i authorities as if Exit Point Manager were not installed.
- *REJECT - Reject the request.
- *SWITCH - Allow the request after switching the request to run under the authority of a different user profile—the switch profile. See Switch Profiles).
- *MEMOS400/*MEMREJECT/*MEMSWITCH - Use the rules specified in a previously memorized transaction. (See Memorizing Transactions).
- *MEMOBJ - Check Object List. (Refer to rules defined for specific objects. See Object Rules.)
Flags
Access Control Rules also include flags. The three flags are Aud (Audit), Msg (Message), and Cap (Capture).
- Audit
- Yes= Record this request to the Audit Journal
- No= Do not record the request (unless request fails)
- Message
- Yes= Send a message when the request is received
- No= Do not send a message
- Capture
- Yes= Capture transactions for this request
- No= Do not capture transactions
* = Inherited from a higher level (such as Change Server Function Rule). When using the browser interface, the "Inherit" check box indicates the value is inherited from a higher level, and the origin of the inherited value is indicated adjacent to the check box. See Active Rule and Rule Derivation.
Switch Profiles
The switch profile action is the key to providing flexible security for your network users. This action lets you specify an alternate user profile, called a switch profile, that network access requests run under. This allows you to use standard IBM i security commands to establish the authorities to objects on your system for a user when they access the system through the network servers.
To define a Switch Profile as part of a rule:
- Set the Authority to *SWITCH.
- Specify the target user.
A typical requirement for *SWITCH profile:
- User belongs to a group profile that owns objects.
- Network access gives the user *ALL authority to the entire application.
- Use Exit Point Manager to allow selective access.
- Dynamically change user authority “on the fly”.
- Give more or less authority than normal.
- *SWITCH profile does not affect green screen operations.
- Can configure authority independently.
For details, see Switch Profiles.
Exit Point Manager always searches for location access rules first
User access rules are considered only if a location access rule is found with an action that indicates that user access rules should be used.
Active Rule and Rule Derivation
When working with User and Location rules, you can use 5, Display, to see the Rule Derivation panel, which provide Active Rule and Rule Derivation information. A value of ‘*’ indicates that Exit Point Manager is inheriting the actual value from another location (much like *SYSVAL in the OS).
Identifying Rule Derivation on the Green Screen
Exit Point Manager has a hierarchy of rules that, when displayed, shows what the current active rule is. For most rules, you can set the values that determine what the rule does to * (or *DEFAULT).
The Rule Derivation screen lets you see the following: 1) For a given rule, which values are set to the default and 2) from which setting did that value come.
For example, suppose there is a rule for user MARKJ and the audit and capture values are all set to *. If that rule is invoked, those asterisks each resolve to either Y or N based on the hierarchy. If all properties are set as shown in the following table, then the Active Rule for user MARKJ is Audit = Y, Message = N, and Capture = Y.
| F | Audit | Msg | Cap |
|---|---|---|---|
| Work with System Values | y | y | N |
| Change Server Function Rule | * | N | * |
| MARKJ (rule) | * | * | Y |
| Then, the Active Rule is | Y | N | Y |
The following screen shows the rule derivation. The asterisks in the Audit and Msg fields in the Rule Derivation section for MARKJ take the values from the levels above. The Active Rule is the rule that results from the Rule Derivation values.
User Rule Detail showing Active Rule and Rule Derivation
- System level details can be changed in the Work with System Values panel.
- Server and server function level details can be changed in the Change Server Function Rule panel.
- User level details can be changed in the Work with Security by User panel.