Add/Modify AWS Cloud Service Account
How to Get There
From the AWS Accounts menu, choose Add AWS Account.
Or, on the Manage AWS Cloud Service Accounts screen, click Add.
Or, click an existing account to modify it.
What it Does
Use this screen to create or modify an AWS account definition.
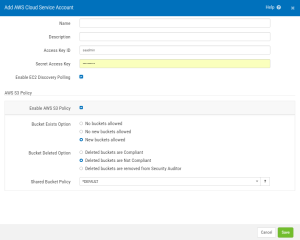
This screen allows you to define access to an Amazon Web Services (AWS) Elastic Compute Cloud account. Security Auditor will interact with this service to detect and automatically monitor the policy settings on these servers.
You can define one or more accounts and associated filter settings that will automatically map AWS server instances to Security Auditor Managed Services with Shared Group Policy definitions.
These options also allow you to enable an S3 policy and define how it is enforced for buckets in the account.
Options
Name
This is a unique name for the account.
Description
An optional description of the account.
Access Key ID • Secret Access Key
The Access Key ID and Secret Access Key of your cloud services account.
Enable Discovery Polling
Check this box to enable server instance discovery. With this option enabled, new servers added to your cloud service will be identified by Security Auditor and added as managed servers based on your filter settings. See the Manage Filters screen and Add/Modify Filter screen.
AWS S3 Policy
Enable AWS S3 Policy
Use this check box to enable or disable an S3 Bucket Policy.
Bucket Exists Option
If Enable AWS S3 Policy is checked, these options are available.
- No buckets allowed. Choose this option to consider any/all buckets in the account non-compliant.
- No new buckets allowed. Choose this option to consider new buckets non-compliant. With this option selected, the first CheckIt establishes the baseline bucket list. New buckets are non-compliant until allowed. (A Policy can be defined on “allowed” buckets.)
NOTE: A 'not allowed' icon
 under the Compliant column in the Manage Service Buckets screen for the account identifies buckets that are not allowed. You can click
under the Compliant column in the Manage Service Buckets screen for the account identifies buckets that are not allowed. You can click  (Add to Baseline) on this screen to add an exception to the 'not allowed' list for a particular bucket.
(Add to Baseline) on this screen to add an exception to the 'not allowed' list for a particular bucket. - New buckets allowed. New buckets are allowed upon which a Policy can be defined.
Bucket Deleted Option
If Enable AWS S3 Policy is checked, these options are available. These options control how Security Auditor reacts when buckets are deleted from the AWS account.
- Deleted buckets are Compliant. Choose this option to consider buckets deleted from the account compliant.
- Deleted buckets are Not Compliant. Choose this option to consider buckets deleted from the account not compliant.
- Deleted buckets are removed from Security Auditor. Choose this option to remove buckets deleted from the AWS account from Security Auditor as well.
Shared Bucket Policy
Select a Shared Bucket Policy object that will be assigned to buckets when they are found in the account.