EFT Server employs an inheritance hierarchy to manage the Server, Site, and user settings, and Group permissions. The administration interface displays this hierarchy as a navigation tree in the left pane on the Server tab.
The tree displays each of the EFT Server components that you configure in the administration interface. When you click an item in the tree, the available tabs in the right pane change based on your selection. For example, when you click a Server (e.g., Local Server) on the Server tab in the left pane, the tabs appear in the right pane for configuring that Server. When you click a user on the Server tab in the left pane, the tabs appear in the right pane for configuring that user.
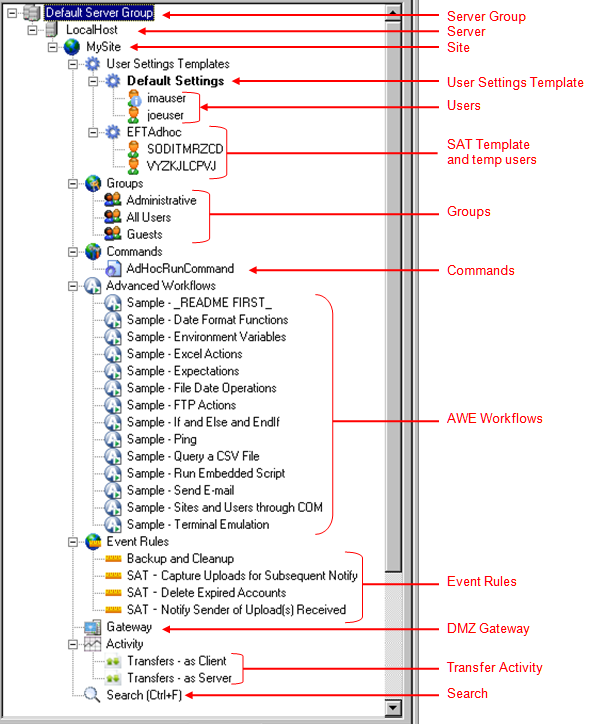
You can create new items and manage items in the tree by right-clicking the tree, or clicking Configuration on the main menu. The illustration below shows the nodes expanded and labeled. Descriptions are below the illustration.

The Server Group node is the topmost level and is an organizational function for multiple groups of Servers; you can add additional Server Groups. (Do not confuse with Permission Groups, below.)
The Server node represents one or more physical EFT Server services running on the local computer or a remote system. Refer to Server Setup Wizard for more information.
The Site node is similar to a virtual host bound to one or more IP addresses. Multiple Sites (or hosts) are allowed within each Server. Configuration of Site-wide settings can be inherited at lower levels (in the Settings Template or per user). Each Site contains its own Settings Templates, Users, Groups, Commands, Advanced Workflows, Event Rules, Gateway node, Activity node, and Search node. Refer to Defining Connections (Sites) for more information.
The User Settings Templates node allows you to apply a setting configuration to an entire group of users. Similar to templates or profiles, Settings Templates are a powerful way of organizing users into groupings with predefined settings. The Settings Template specified as the default appears in the tree with bold text.
Users are individual accounts or partners assigned to a Settings Template. Each user can be configured to inherit settings from the Settings Template or have specific settings defined for that particular user. When a user account is disabled, the user icon and a red circle with an X on it ![]() . A user account without a defined e-mail address has a blue circle with an i on it
. A user account without a defined e-mail address has a blue circle with an i on it![]() .
.
The Groups node allows you to define user access permissions to files and folders. Groups are assigned on the Site. Users' access to folders and files are defined by their assigned Group's permissions.
The Commands node allows you to configure Commands that launch external executables, batch files, or scripts. Once configured, these Commands can be called from within an Event Rule.
The Advanced Workflows node allows you to visually design programmatic workflows without prior programming experience. You can "drag-and-drop" from a list of hundreds of predefined actions to create sequenced workflows according to your business logic. Once configured, these workflows can be called as individual actions from within an Event Rule
The Event Rules node consists of triggering Events, optional Conditions affecting the Event Rule, and the resulting Actions that are carried out. For details, refer to Introduction to Event Rules.
The Gateway node allows you to configure the IP address, port, and protocols used to communicate with DMZ Gateway.
The Activity node allows you to view transfer activity to and from the Site.
The Search node allows you to search the selected Site for a specific user, Event Rule, Command, etc.